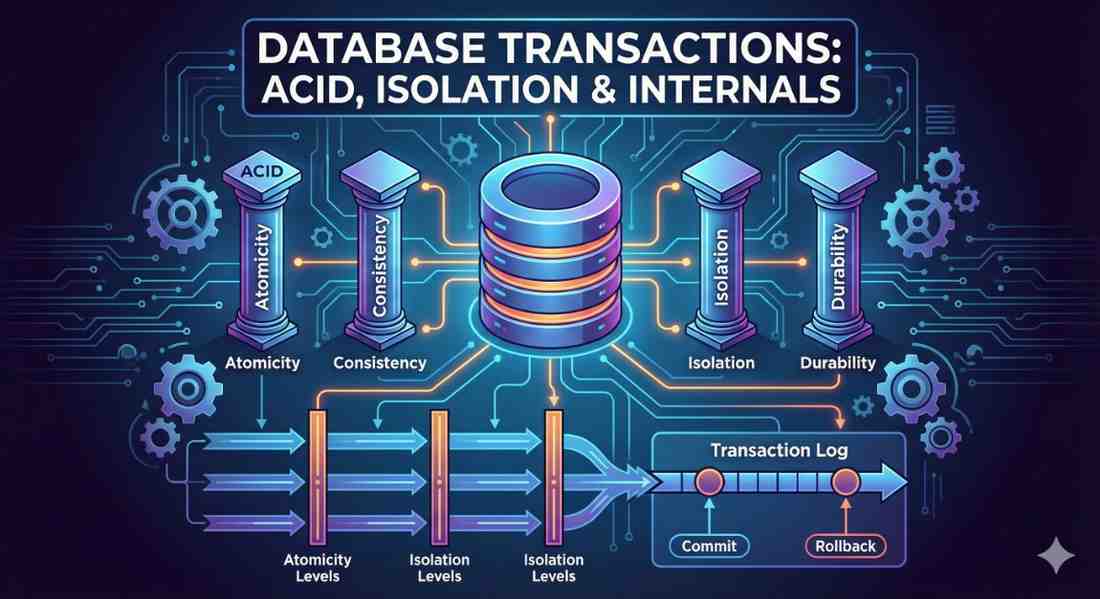
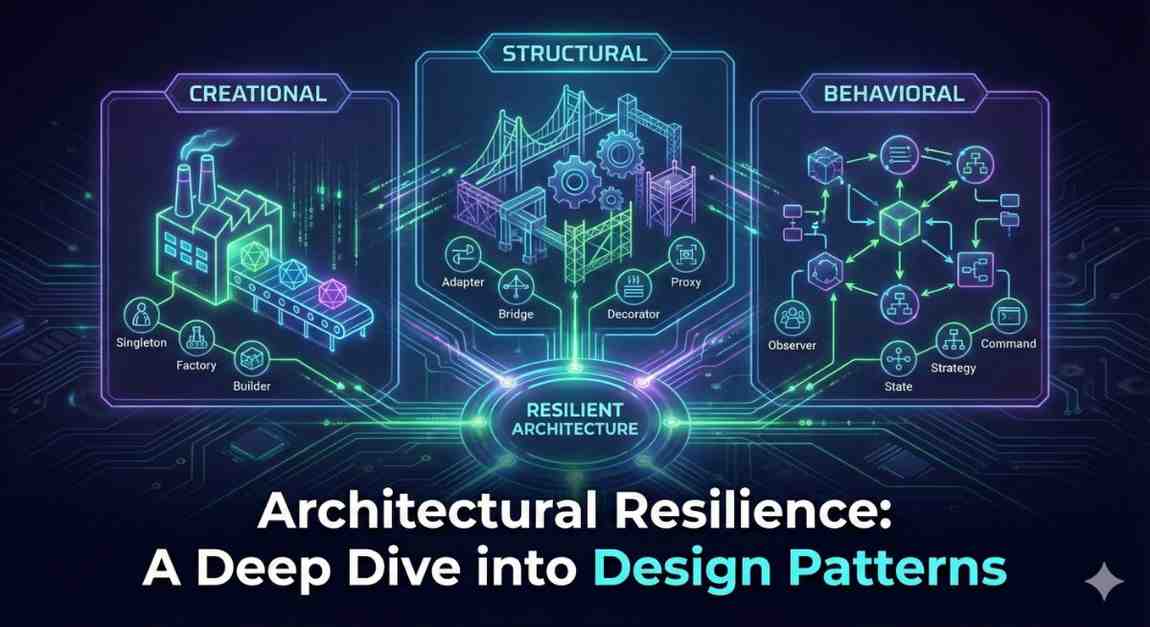
Mastering Server-Side Logic in Microsoft SQL Server
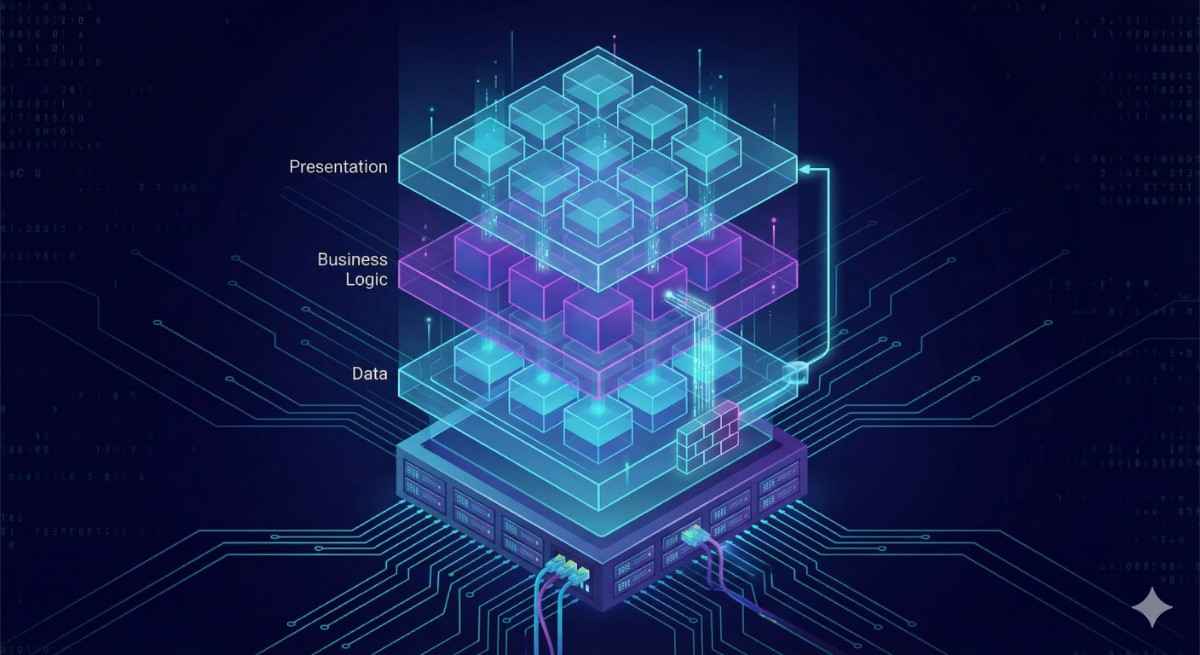
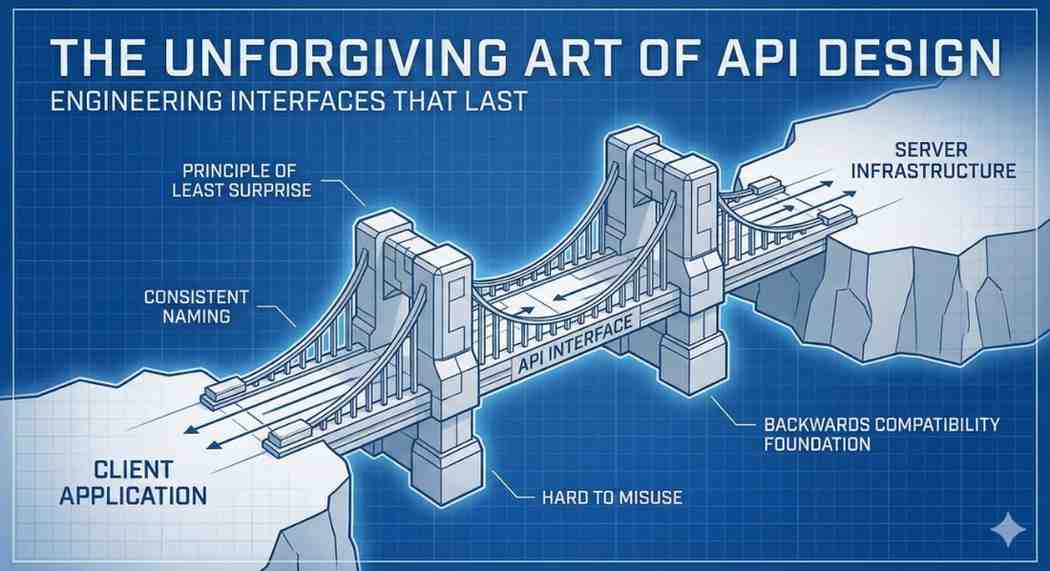
As software engineers, we often debate where business logic should reside. Should it be entirely in the application layer (C#, Java, Python) or within the database itself? While modern trends often...