
Object-Oriented Design Principles
You write a feature, it works perfectly, and you deploy it. Two months later, a simple requirement change comes in, and suddenly you’re rewriting half the application. Why? Because while the code w...

You write a feature, it works perfectly, and you deploy it. Two months later, a simple requirement change comes in, and suddenly you’re rewriting half the application. Why? Because while the code w...
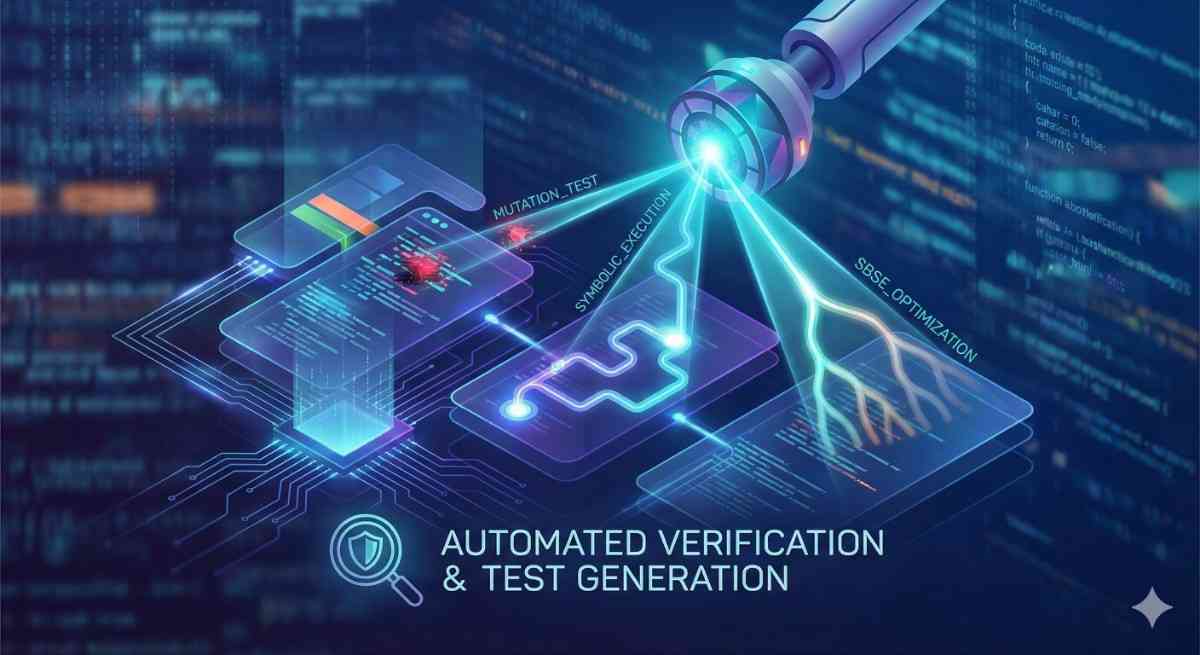
Software engineers often treat testing as a chore—a box to check before deployment. However, digging deeper into Automated Software Engineering reveals that testing is less about writing assertions...
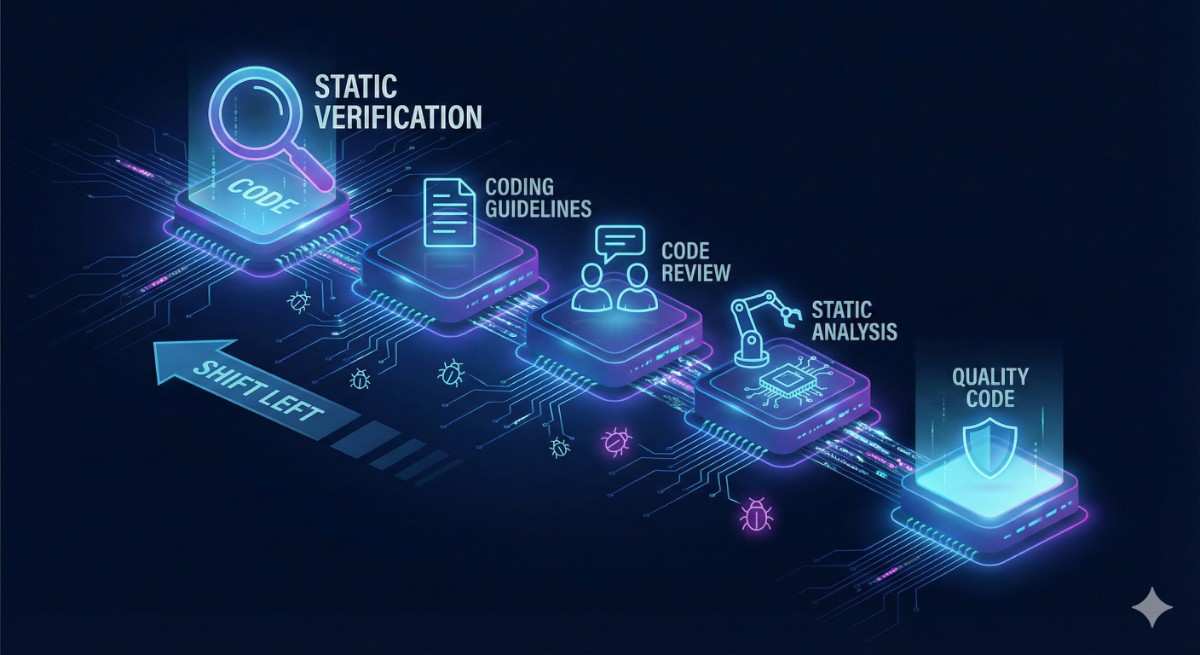
In the modern software development lifecycle (SDLC), the cost of fixing a bug grows exponentially the later it is discovered. A defect found in production might cost 100x more to fix than one found...

As penetration testers and software engineers, we often obsess over dynamic attacks—SQL injection payloads, XSS vectors, and runtime exploits. But what if you could catch the vulnerability before t...

As penetration testers and software engineers, we spend a lot of time breaking things. We write unit tests, we run fuzzers, and we manually hammer APIs looking for edge cases. But there is always ...
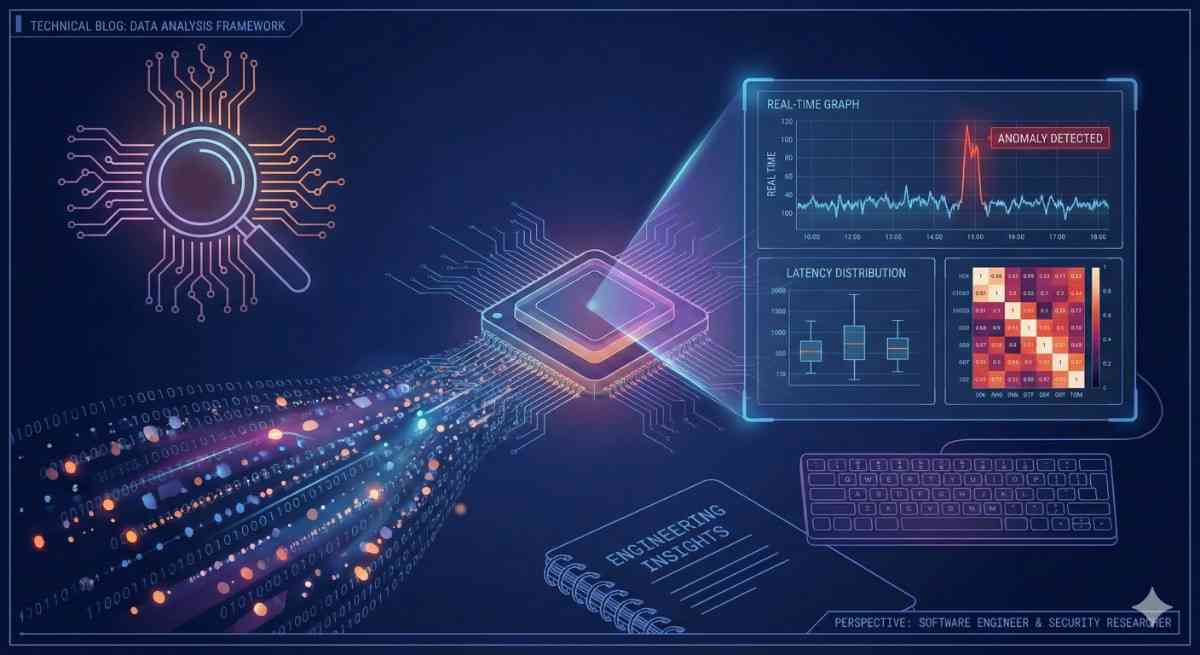
In our field—whether you are debugging a distributed system, hunting for security anomalies, or optimizing software performance—we are often drowning in data but starving for insights. "Data Analys...

The landscape of software development tools is undergoing a fundamental shift. For decades, our “intelligent” tools—IDEs, linters, and refactoring engines—were built on deterministic logic. Today, ...
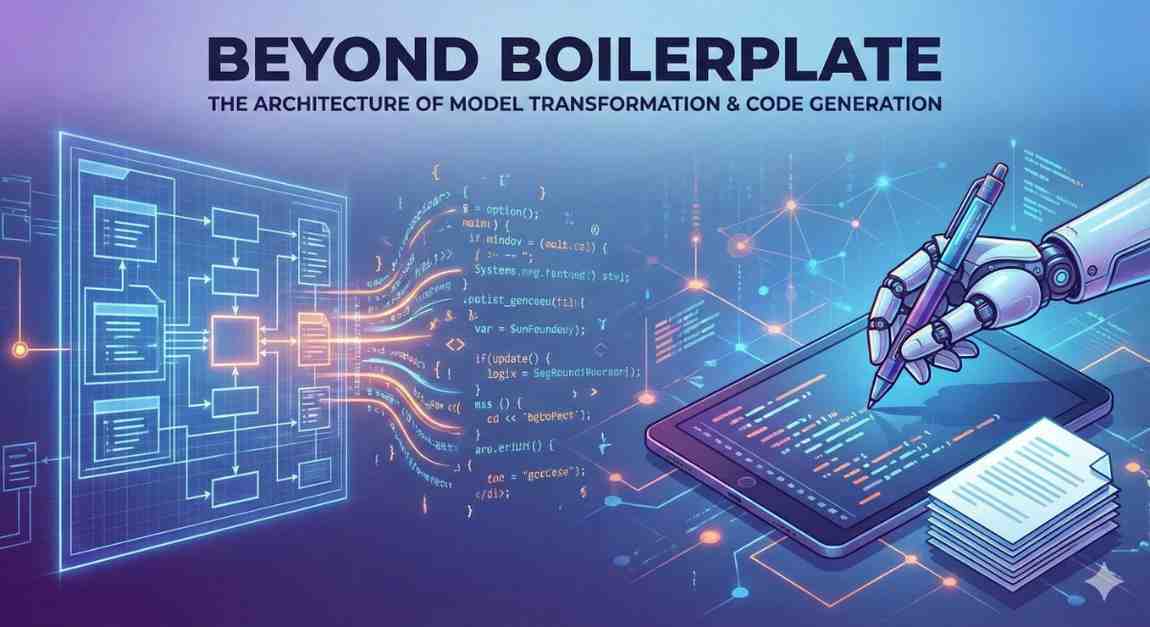
In modern software engineering, we often find ourselves repeating the same patterns: setting up CRUD endpoints, defining database schemas, or writing serialization logic. As engineers, our instinct...
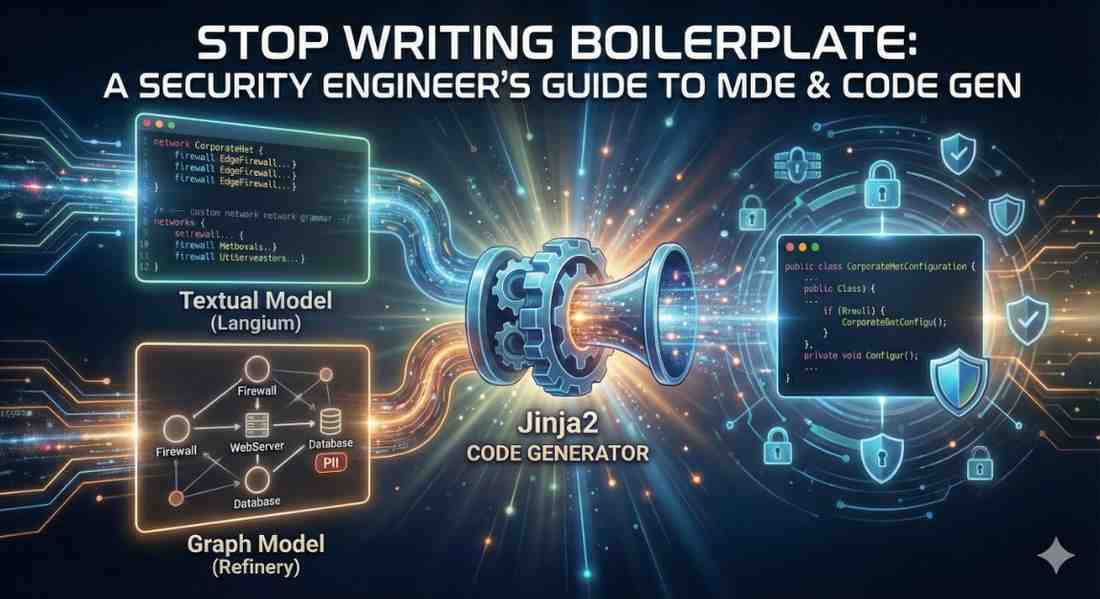
If you are studying software engineering or getting into Application Security, you know the pain of “Boilerplate.” You spend hours writing the same setup code—configuring firewalls, setting up data...

In modern software engineering, ensuring reliability goes beyond writing happy-path unit tests. As logic complexity increases, manual testing becomes insufficient for catching edge cases and state-...