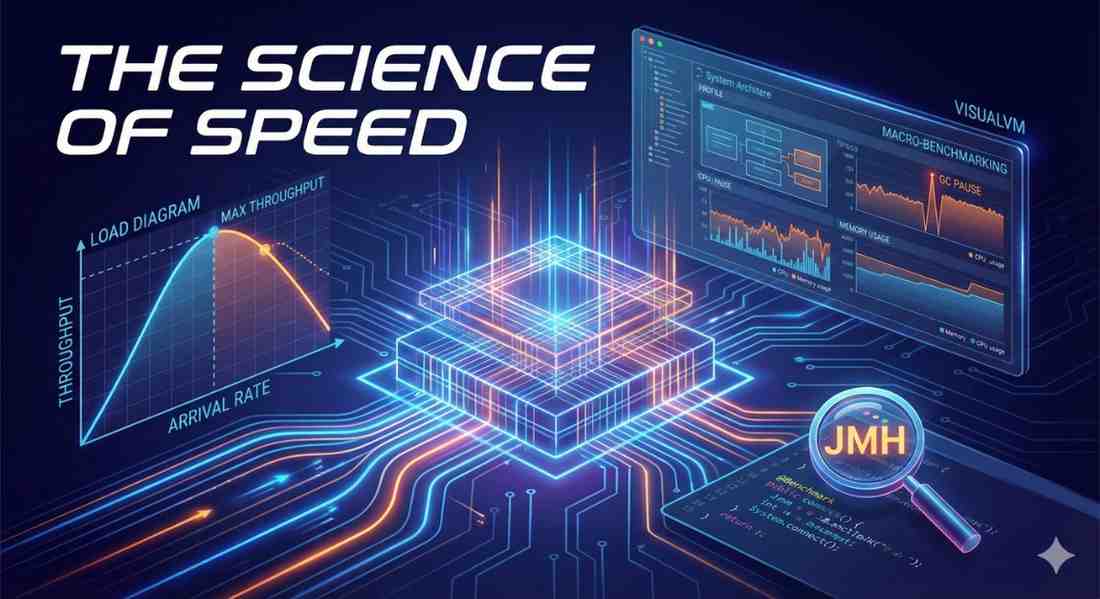
Software Performance Benchmarking
In software engineering, “fast” is a subjective term; “throughput of 10,000 operations per second” is an objective fact. However, deriving that fact requires more than just running a timer around a...

In software engineering, “fast” is a subjective term; “throughput of 10,000 operations per second” is an objective fact. However, deriving that fact requires more than just running a timer around a...
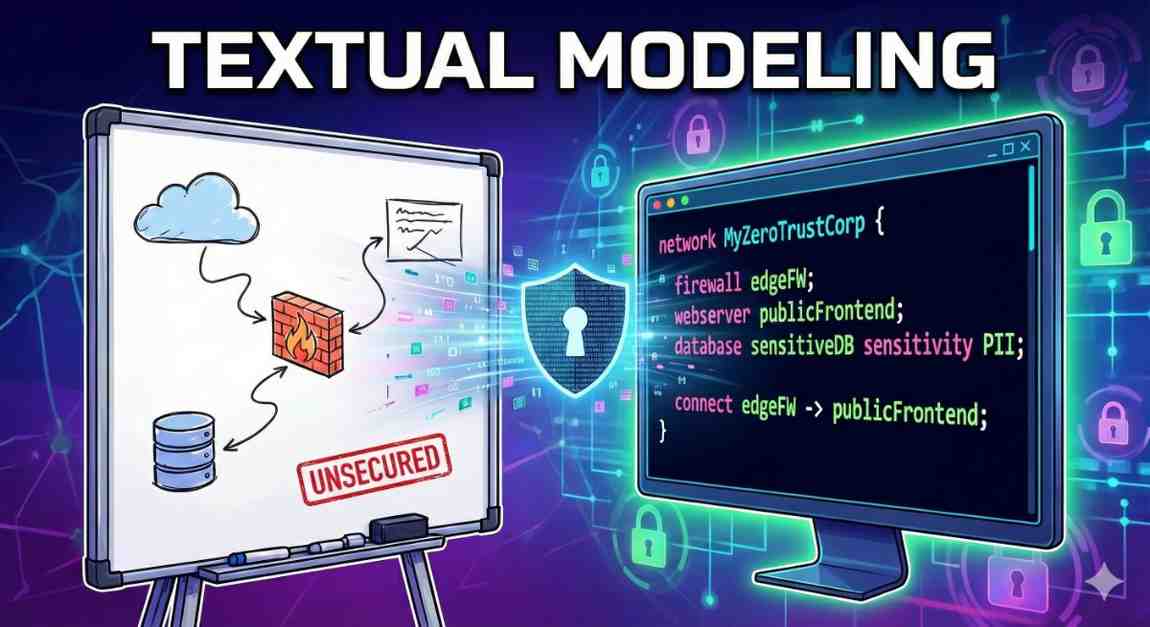
If you’ve followed my posts on penetration testing and app sec, you know the struggle of architectural diagrams. You draw a “Secure Network” on a whiteboard or in Visio: a Firewall here, a Database...
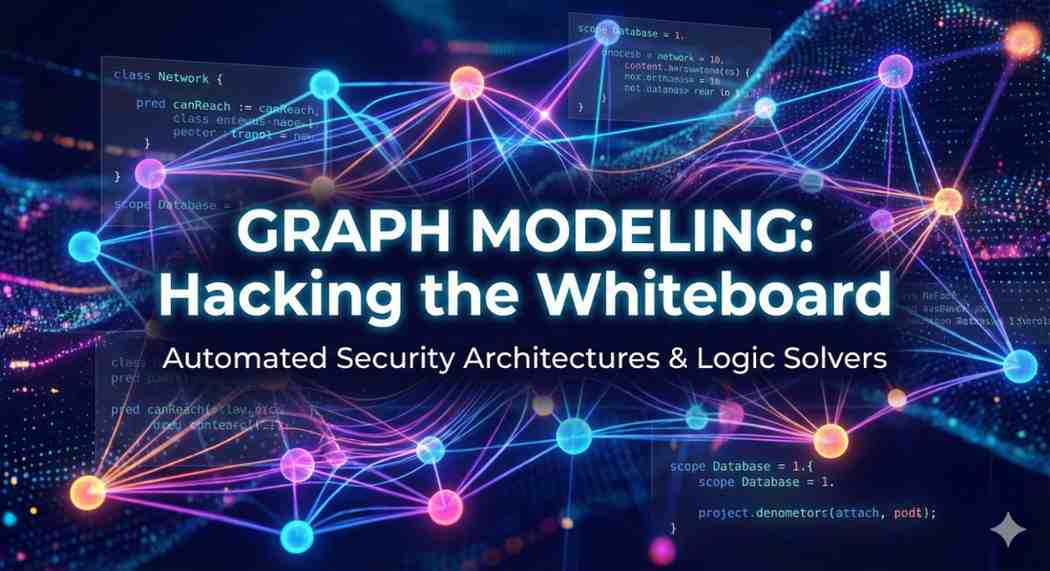
If you’ve ever tried to secure a complex system, you know the struggle: you draw a diagram on a whiteboard, you think it looks secure, but you missed one hidden path that allows an attacker to bypa...
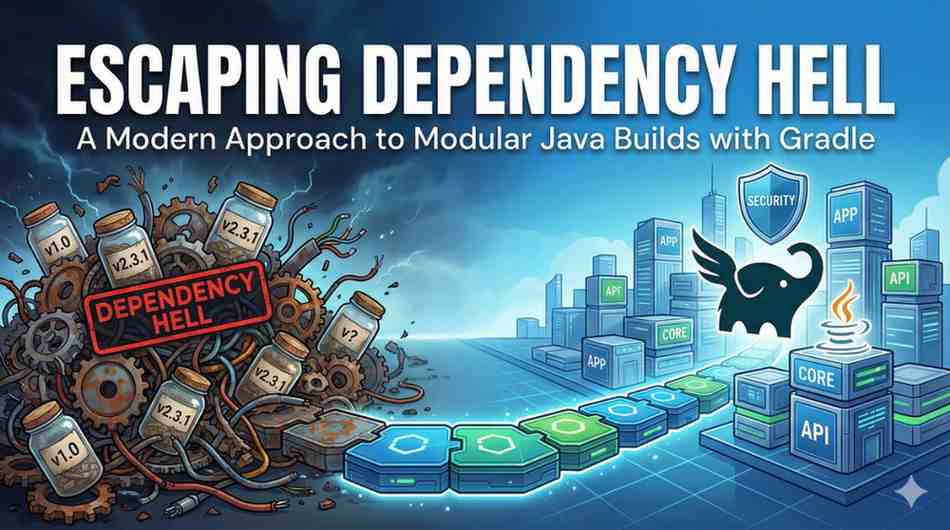
As software engineers and security practitioners, we often focus on the code itself—the logic, the vulnerabilities, the architecture. But the machinery that builds that code is often neglected. We’...

In software engineering and application security, unpredictability is the enemy. If your build process is flaky, manual, or opaque, you cannot guarantee the security of the final product. You canno...

1. Executive Summary Vulnerability: Mass Assignment. Description: The application’s checkout endpoint (POST /api/checkout) accepts a JSON object representing the order. The backend framework auto...

1. Executive Summary Vulnerability: Broken Object Level Authorization (BOLA) / Mass Assignment via Hidden Method. Description: The application exposes an API endpoint to retrieve product prices (...

1. Executive Summary Vulnerability: Information Disclosure (Exposed API Documentation). Description: The application exposes its full API schema (Swagger/OpenAPI interface) at a predictable path ...

1. Executive Summary Vulnerability: Flawed Brute-force protection in password change functionality Description: The “Change Password” functionality behaves inconsistently based on whether the two...

1. Executive Summary Vulnerability: Broken Password Reset (Token Validation Bypass). Description: The application implements a password reset flow that includes a token in the URL and form body. ...